Vulnerability scans play a critical role in protecting assets from attacker exploitation by identifying missing updates, misconfigurations, and other common security issues. Originally designed to test local networks and devices, vulnerability scanning tools have evolved to encompass the modern IT environment as well as specialized tools for specific vulnerabilities, assets, and applications.
Top Vulnerability Scanners
- Invicti: Best Website and Application Vulnerability Scanning Tool
- Nmap: Best Open Source Specialty Port Scanner
- OpenVAS: Best Open Source IT Infrastructure Vulnerability Scanner
- RapidFire VulScan: Best MSP / MSSP Option
- StackHawk: Best SMB DevOps App Scanner
- Tenable.io: Best Enterprise Integrated Vulnerability Scanning Tool
- Vulnerability Manager Plus (ManageEngine): Best for SMB IT Infrastructure Scans
- Wiz: Best Cloud & Kubernetes Vulnerability Scanning Specialist
For those interested in our methodology, we provide a summary after discussing the tools as well as tips for selecting and effectively using vulnerability scanning tools.
For those who need a quick refresher of Vulnerability scanning consider reading this article first: What is Vulnerability Scanning? Definition, Types & Guide.
1 Intruder
Intruder is the top-rated vulnerability scanner. It saves you time by helping prioritize the most critical vulnerabilities, to avoid exposing your systems. Intruder has direct integrations with cloud providers and runs thousands of thorough checks. It will proactively scan your systems for new threats, such as Spring4Shell, giving you peace of mind. Intruder makes it easy to find and fix issues such as misconfigurations, missing patches, application bugs, and more. Try a 14-day free trial.
Invicti: Best Website and Application Vulnerability Scanning Tool
Although related to network, cloud, and other IT infrastructure vulnerability scanning tools, website and application vulnerability scanning tools apply specialized algorithms to search for programming vulnerabilities. Invicti, formerly known as Netsparker, is a popular application vulnerability scanner designed for enterprise-scale and automation.

Key Features
- Automatic and continuous scans to update website, application and API inventories
- Avoids scanning queues by allowing multiple concurrent scans and scanners that feed into a centralized repository for reporting
- Deploys on-premises, in the cloud, within Docker images, or as a hybrid solution. Cloud agents launch for scans then self-delete when the scan is completed
- Dynamic and automatable Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and Software Composition Analysis (SCA) scanning
- Out-of-band testing and asynchronous vulnerability testing
- IAST sensors can often provide file name and programming line number for vulnerabilities
- Crawls pages authenticated by form submission, OAuth2, NTLM/Kerberos and more
- Scans complex paths and multi-level forms, password-protected areas, script-heavy sites (JavaScript or HTML5), single page applications (SPAs), unlinked pages
Pros
- Scans hidden files
- Detects misconfigured configuration files
- Industry leading detection and false positive rates from independent tests
- Will track security posture for applications over time and identify vulnerability trends
- Actively reduces false positives and can verify vulnerabilities and provide proof of exploit
- Integrates with pipeline tools and issue trackers such as Jenkins, Jira, and GitHub for developer workflow integration
Cons
- Can have a steep learning curve
- Customers complain about ineffective multi-factor authentication testing
- Users notice slowness in the scans on larger web applications
- Only available with a Windows software installation
Pricing
Invicti publishes neither pricing information nor licensing levels on their website. Invicti offers three plans:
- Standard on-premises desktop scanner
- Team scanner (hosted) adds additional features over desktop scanner:
- Multi-user platform
- Built-in workflow tool
- PCI Compliance scanner
- Asset Discovery
- Enterprise (hosted or on-premises) adds custom workflow and dedicated tech support
For more information on Invicti and competing application vulnerability scanning tools, read Best DevOps, Website, and Application Vulnerability Scanning Tools.
Nmap: Best Open Source Specialty Port Scanner
Developed originally for Linux, the Nmap Security Scanner supports binary packages for Windows, macOS, and Linux. Nmap uses IP packets as a port scanner to determine what hosts, services, and operating systems are available from a device. Penetration testers and IT teams value nmap as a quick, effective, and light-weight tool to list open ports on a system.
For more information, see also: Nmap Vulnerability Scanning Made Easy: Tutorial
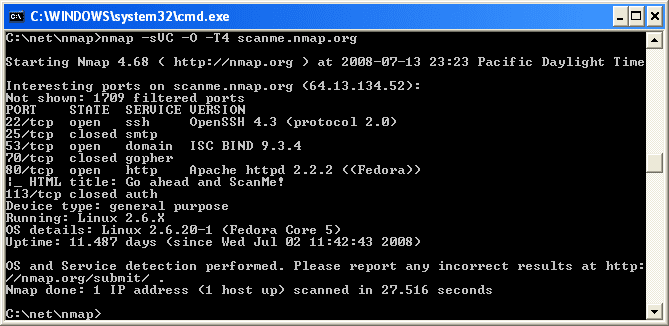
Key Features
- Host discovery quickly determines IP addresses up and available on a network
- Uses TCP/IP stack characteristics to guess device operating systems
- Growing library of 500 scripts for enhanced network discovery and vulnerability assessment
Pros
- Quickly scans open ports on a system and determines available TCP/UDP services
- Interrogates ports to determine running protocols, applications and version numbers
- Large user base and open source community
Cons
- No formal support for customers
- Requires some expertise and IT knowledge to use effectively
- Does not natively rank vulnerabilities, verify vulnerabilities, or integrate with vulnerability management tools and ticketing platforms
Pricing
Nmap is an open source tool available for free to end users. Companies that want to integrate Nmap into commercial products need to license the software.
OpenVAS: Best Open Source IT Infrastructure Vulnerability Scanner
Before Tenable stopped offering the open-source Nessus tool, developers forked the code and created the OpenVAS (Open Vulnerability Assessment Scanner) tool. Greenbone Networks began supporting development of this open-source tool in 2006. Although developed as a Unix/Linux scanner, OpenVAS can scan for a broader range of vulnerabilities, including Windows OS vulnerabilities.
Key Features
- Scans systems for known vulnerabilities and missing patches
- Web-based management console
- Can be installed on any local or cloud-based machine
- Provides insights on the vulnerability such as how to eliminate the vulnerability or how attackers might exploit the vulnerability
Pros
- Free, open source tool
- Large community for peer support
- Source code available for review
- Regularly updated and features added periodically
Cons
- Not as user-friendly as commercial tools; better for experts
- Large numbers of concurrent scans may crash the program
- Very technical, no frills reporting
Pricing
OpenVAS is available for free.
For more information on Nmap, OpenVAS and other open-source vulnerability scanning tools read 10 Best Open-Source Vulnerability Scanners for 2023.
RapidFire VulScan: Best MSP/MSSP Option
Managed IT service providers (MSPs) and managed IT security service providers (MSSPs) play a key role in detecting and prioritizing vulnerabilities for many organizations with IT resource constraints. RapidFire tool’s VulScan product performs internal and external network vulnerability scans. This tool can be combined with their Network Detective Pro and Cyber Hawk tools to enable MSPs and MSSPs to deliver a broad range of IT and security services.

Key Features
- Automate internal vulnerability scans
- Multiple scanners can be scheduled independently, but results consolidate to one dashboard
- Supports multiple clients with consolidated and individual dashboards and reports
- Automatically generate service tickets for discovered issues and vulnerabilities
- Multi-tenant dashboards
- Automated email alerting, filtered by desired IP ranges or severity
- Use custom scans for specific needs or quickly set up the scanner and use preset scans for “Low Impact,” “Standard,” and “Comprehensive”
- More thorough scans can be enabled using authenticated or credentialed scanning from internal endpoints
Pros
- External and internal vulnerability scanners enable MSPs and MSSPs to deliver vulnerability management and remediation services
- The brandable and customizable report generator enables MSPs and MSSPs to create branded reports or to help customers provide customer-branded compliance reports
- Service-provider-specific training resources
- Optional workflow to outsource alerts to RocketCyber SOC
- Partner white-label marketing materials
Cons
- For-pay onboarding can be too short for effective training
- Virtual appliance requires expertise to set up correctly
Pricing
RapidFire Tools does not post pricing, but instead requests that interested customers fill out a form for a quote. Customers have reported prices in the range of $500 per scanner for a multi-year commitment.
For more information on RapidFire VulScan and other MSP/MSSP-friendly vulnerability scanning tools, read Best MSP / MSSP Vulnerability Scanning Tool Options.
StackHawk: Best SMB DevOps App Scanner
Founded by DevOps engineers for DevOps engineers who write and push out code every day, StackHawk seeks to simplify the process of building secure software. Their DAST scanner integrates with CI/CD Automation and Slack to help triage findings and enable rapid correction.
Key Features
- CI/CD and Slack Integration
- REST, GraphQL and SOAP support
- Custom scan discovery and historical scan data
- cURL-based reproduction criteria
Pros
- Unlimited scans for one application
- Unlimited scans and environments
- Docker-based application security scanner
- Continues to add features to the free tool (gRPC support in development)
Cons
- Requires use and knowledge of Docker infrastructure
- Only provides email based support for the free version
- Requires a paid license for more than one application
Pricing
Stack Hawk offers three levels of licensing. Paid versions are based on a price of per developer per month and can be billed monthly. Annual billing results in a discount for the paid tiers.
- Free Tier – Only one application
- $49 / developer per month Pro Tier
- Minimum 5 developers, volume discounts available
- Unlimited application scanning
- Free Tier features plus: Applications dashboard, Snyk integration, GitHub CodeQl and Repo integration, Custom Test Data for REST, HawkScan ReScan, and custom Test Data for GraphQL
- Support via email and Slack
- $69 / developer per month Enterprise Tier
- Volume discounting available
- Pro Tier features plus many other features including: Single Sign-on, MS Teams, Webhooks integration, role-based permissions, executive summary reports, API access for scan results, policy management
- Support via email, slack (dedicated support), and an option for Premier Zoom support
For more information on StackHawk and other SMB-friendly vulnerability scanning tools, read Best Small and Medium-sized Business (SMB) Vulnerability Scanning Tools.
Tenable.io: Best Enterprise Integrated Vulnerability Scanning Tool
Tenable.io builds off of the popular Nessus tool to provide vulnerability scanning capabilities for more than 47,000 unique IT, IoT, OT, operating systems, and applications. The tool integrates with the broader Tenable One platform, which includes vulnerability management and web app scanning as well as the tenable.sc security center. Tenable conducts regular research and discovers zero-day vulnerabilities that it adds to the tool for early detection.
Key Features
- Preconfigured templates to enable quick starts
- Automatically performs full scans as soon as new vulnerability plugins are added
- Checks for vulnerabilities as well as compliance configurations
- Report templates provide quick snapshots
- Customizable templates enable branded reports for consultants and service providers
- Automated vulnerability and misconfiguration alerts for Security Incident and Event Management (SIEM) tools
Pros
- 3rd Easiest to Use in Vulnerability Scanner software rankings on G2
- Executive dashboards and powerful filtering to dig into findings
- Can assess modern infrastructure as code (IaC)
- Agentless Scanning
Cons
- Steep learning curve for new users
- Some users complain of false negatives
- Some users complain about limited API integration
Pricing
Tenable provides their products based on annual subscriptions with multi-year discounts. They offer the less comprehensive Nessus product in three versions and two levels of pricing for Tenable.io:
- Tenable.io Vulnerability Management
- Pricing based per asset (minimum 65)
- $2,275 / year for 65 assets; discounts for multiple year contracts
- Tenable.io Web App Scanning
- Pricing per domain starting at 5 fully qualified domain names
- $3,578 / year for 5 domains
- Nessus Professional
- Unlimited IT and configuration assessments
- $3,390 / year with options for advanced support and on-demand training
- Nessus Expert: The capabilities of Nessus Pro plus
- External attack surface scanning
- Cloud infrastructure scanning
- 500 prebuilt scanning policies
- Ability to add domains
- $7,490 a year with options for advanced support and on-demand training
- Nessus Essentials edition:
- Free, but limited capabilities
- Up to 16 IP addresses per scanner
- No compliance checks or content audits
- No technical support
- One-time use. New installations require a new license
Free trial versions are available for the commercial products. Resellers may offer discounted or bundled pricing.
For more information on Tenable.io and competing enterprise vulnerability scanning tools, read Best Enterprise Vulnerability Scanning Vendors.
Vulnerability Manager Plus (ManageEngine): Best for SMB IT Infrastructure Scans
ManageEngine offers a wide variety of identity, IT management, and security solutions. Their Vulnerability Manager Plus product scans devices and web servers to detect vulnerabilities, misconfigurations, and high-risk software. For small businesses with under 25 devices, ManageEngine offers a free license.
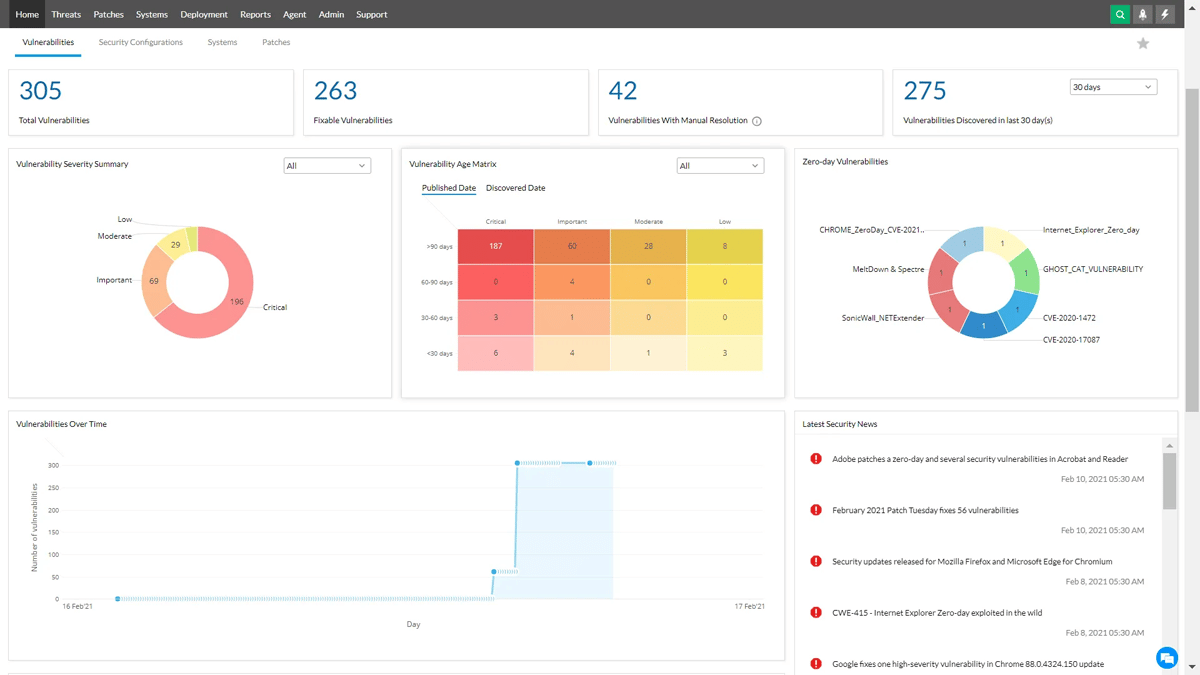
Key Features
- Scans devices for vulnerabilities in operating systems and third-party software, end-of-life software, peer-to-peer software, as well as zero-day vulnerabilities
- Scans for default credentials, firewall misconfigurations, open shares, and user privilege issues (unused users or groups, elevated privileges, etc.)
- Can scan web servers for unused web pages, misconfigured HTTP headers/options, expired certificates, and more
Pros
- Combines vulnerability assessment, compliance, patch management, and system security configuration into one tool
- Open port detection on all devices
- Easy to set up
Cons
- Does not support AIX OS
- Not Cloud native and does not support automatic deployment of agents on the cloud
- Immediate patch deployment may be limited
Pricing
Free trials are available for three editions of the software licensed annually:
- Free (SMB up to 25 devices)
- Professional: starts at $695 for 100 workstations / 1 technician
- Enterprise: starts at $1,195 for 100 workstations / 1 technician and adds:
- Audit compliance with CIS benchmarks
- View, upload and deploy firmware patches
- Manage and monitor deployment
- Patch Management
- Distribution server
- Schedule remote shutdown
- Schedule Wake on LAN
Management of network devices requires additional licenses.
For more information on Vulnerability Manager Plus and competing SMB-friendly vulnerability scanning tools, read Best SMB Vulnerability Scanning Tools.
Wiz: Best Cloud & Kubernetes Vulnerability Scanning Specialist
Wiz developed their cloud-native Cloud Infrastructure Security Platform to focus on the needs of virtualized infrastructure, containers, and the cloud. Wiz scans multi-cloud, Platform-as-a-Service (PaaS), virtual machines, containers, serverless functions, and other cloud infrastructure without affecting business operations or stealing resources from active workloads and processes.

Key Features
- Native connections to AWS, Azure, Google Cloud, Oracle Cloud and Alibaba Cloud
- Built-in support for Kubernetes on multiple platforms
- Can scan infrastructure-as-code and cloud infrastructure entitlement management
- Incorporates zero-day risks sourced from the Wiz research team
Pros
- Agentless scanning
- Cloud native solution for cloud infrastructure
- 2nd Easiest to Use in Vulnerability Scanner software rankings on G2
Cons
- Users report setup can be cumbersome and tedious
- Integrations can be difficult or incomplete
- Actions must be established for each project for scanning they cannot be cloned
Pricing
Wiz does not list pricing on their website but does offer custom pricing for customers. A 12-month contract for the Cloud Infrastructure Security Platform is listed on the AWS marketplace as $300,000 for all five product levels (Standard, Essential, Essential Plus, Advanced, Advanced Plus).
For more information on Wiz and coverage on other cloud vulnerability scanning tools read the Best 3 Cloud, Container, and Data Lake Vulnerability Scanning Tools.
How the Top Vulnerability Scanning Tools Were Selected
Our research team at eSecurity Planet evaluated tools for this article based on an in-depth review of features and competitors, industry ranking and review sites such as G2 and Gartner Peer Insights. Industry sites such as SecTools.org and the WAVSEP DAST Benchmark were consulted but not weighted heavily since they do not seem to have been updated in several years.
To be included, tools needed to be primarily vulnerability scanning tools so penetration testing, asset management, patch management, vulnerability management, vulnerability management as a service, or security tools (endpoint, network, etc.) that include a vulnerability scanning function were not generally included. We assume the readers are looking for specific tools for vulnerability scanning and we have published other articles on those topics.
Candidate tools were then classified into categories and the top contenders can be reviewed in the following articles:
- 10 Best Open-Source Vulnerability Scanners for 2023
- Best DevOps, Website, and Application Vulnerability Scanning Tools
- Best Enterprise Vulnerability Scanning Vendors
- Best MSP / MSSP Vulnerability Scanning Tool Options
- Best Small and Medium-sized Business (SMB) Vulnerability Scanning Tools
- Best MSP / MSSP Vulnerability Scanning Tool Options
From each category, we selected the best options at the time of writing in our analysis. For open source and SMB-friendly tools, two each were selected; one for IT infrastructure and one for applications. The addition of features, new pricing tiers, and other product changes will force this list to evolve over time and an organization will always need to compare available features against existing needs.
Tips on Using Vulnerability Scanning Tools
Different vulnerability scanning tools will have different priorities and capabilities. A typical organization will need to use several different vulnerability scanning tools to obtain a complete picture of their environment.
An organization will also need to select an appropriate tool for their needs and capabilities. Price and reviews only provide appropriate perspective in context of the tool’s capabilities.
Can You Use Multiple Vulnerability Scanning Tools?
In some cases, an organization can purchase multiple tools from the same vendor, such as a cloud module and a network module from one of the Enterprise Options. Other times, an organization may pick up a network scanner suitable for small businesses and complement it with open source tools for port and application vulnerability scanning.
In many cases, the best solution may be a combination of tools so a security team can perform multiple scans or use redundant scanning tools to compare results. For example, many hackers use open source tools so an organization can use them to locate vulnerabilities most likely to be detected by external hackers. They can then compare against an enterprise tool to help with their internal prioritization and analysis of false positives.
For more insight into vulnerability assessments, read: How to Conduct a Vulnerability Assessment: 5 Steps toward Better Cybersecurity.
How Do You Select a Vulnerability Scanning Tool?
When evaluating vulnerability scanning tools, there are several key considerations to match the needs of the organization against the potential tool:
- Does the vulnerability assessment team have the technology level required to use the tool with ease? A tool too difficult or too time-consuming for the existing team to use will not yield useful results.
- Does the vulnerability assessment tool scan the necessary assets? The best web application scanner in the world cannot effectively scan endpoint operating system vulnerabilities.
- Does the tool deploy flexibly or where needed? A tool delivered as an appliance might not be the best tool to scan a cloud environment when a virtual appliance can be used instead.
- Does the tool provide useful information? The bare minimum tools deliver potential vulnerabilities, while more advanced tools verify results to reduce false positives, prioritize vulnerabilities, and provide intuitive dashboards for quick analysis. The best tools integrate with IT or DevOps ticketing systems or a vulnerability management solution so that vulnerabilities can be tracked, addressed, and reported as resolved.
These four questions address the most critical issues, but the details also matter. Some organizations will also need to consider if reports generated by the tool meets compliance needs; if the tool minimizes impact on users with lightweight agents, distributed scanning, or agentless scanning; if the solution can provide scans from inside and outside of the firewall; and other factors beyond the scope of this article.
Bottom Line: Vulnerability Scanning is the Start of the Process
The security of any organization depends on this process of identifying vulnerabilities and resolving them before attackers can exploit them. Conducting a vulnerability scan provides the starting point for the process of addressing vulnerability risk. Once a vulnerability list is generated, the list must be prioritized and addressed.
The first step will be to verify each vulnerability and eliminate the possibility of false positives. A good vulnerability scanner can prioritize the vulnerabilities by their risk of being exploited, but the team addressing vulnerabilities will also need to ensure the priorities include the value of the asset. Penetration testing tools, internal red teams or hacker consultants can be used to test vulnerabilities, but this expense may only be worth it for high value assets at risk.
A vulnerability management tool or an effective IT or security ticketing tool needs to be deployed to track the progress of the teams addressing the vulnerabilities. To satisfy compliance and internal needs, the management tools or vulnerability scanners will need to be able to provide regular reports on the status of the organization, existing vulnerabilities, and vulnerabilities resolved. For smaller teams, an organization can consider vulnerability-management-as-a-service (VMaaS) to offload the tasks. Execution of this cycle of vulnerability discovery, remediation, and reporting provides assurance to stakeholders that the risk of the organization is effectively addressed.
To explore the concept in more depth, consider reading the following articles:


