The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is recommending that government agencies and private organizations that use Microsoft’s Exchange cloud email platform migrate users and applications to Modern Auth before Basic Auth is deprecated in October.
CISA noted that Basic authentication is simple and pretty convenient but unsecured by design. It’s relatively easy for any motivated attacker to intercept the data that is often transmitted in plain text or encoded with reversible algorithms such as base64.
Basic Auth exposes servers and other endpoints to MITM (Man In The Middle) and password spraying attacks. And it’s incompatible with multi-factor authentication (MFA) systems, so admins might be discouraged from enabling it.
In contrast, Modern Auth that relies on OAuth 2.0 or Microsoft Active Directory Authentication Library uses tokens that expire quickly and cannot be reused elsewhere.
While CISA released its guidance for government agencies, all organizations are urged to switch to Modern Auth before October 1, when Microsoft has said that Basic Authentication will be turned off for all protocols.
Also read: OAuth: Your Guide to Industry Authorization
How to Migrate Exchange Authentication
CISA recommends implementing an authentication policy for all Exchange Online mailboxes and disabling Basic authentication:
- Navigate to the M365 Admin Center’s Modern Authentication Page: https://admin.microsoft.com/#/homepage/:/Settings/L1/ModernAuthentication.
- Ensure turn on modern authentication for Outlook 2013 for Windows and later is checked. This is the default setting.
- Uncheck every protocol under Allow access to basic authentication protocols.
- Click Save.
Orgs can configure a Conditional Access policy that applies specifically to legacy authentication clients and blocks access:
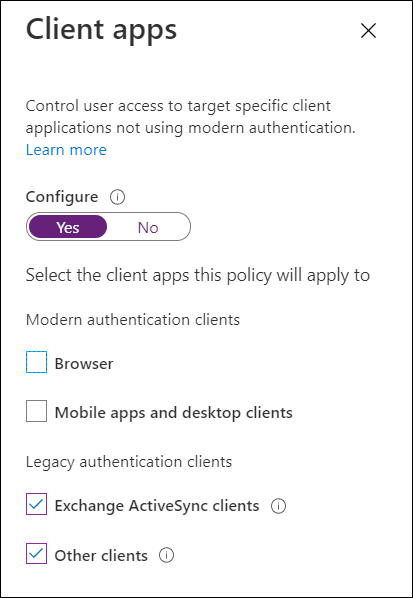
The CISA announcement is actually a reminder, as the Microsoft Exchange team has been disabling Basic auth in tenants that weren’t using it since 2021. Indeed, this obsolete authentication has been held responsible for massive leaks in plain text.
Because many orgs are still using it, Basic auth is now deprecated, and customers will have to migrate one way or another.
Customers can set their Authentication Policies to control the migration (e.g. date and time). Otherwise, the Exchange team “will randomly select tenants, send 7-day warning Message Center posts (and post Service Health Dashboard notices), then we will turn off Basic Auth in the tenants.”
Read next: Top Secure Email Gateway Solutions

