The post What is Dynamic Application Security Testing (DAST)? appeared first on eSecurityPlanet.
]]>The cyber security team adopts the role of a simulated hacker and expertly scrutinizes the application’s defenses, thoroughly assessing its vulnerability to potential threats. By doing this, DAST helps determine how secure the web application is and pinpoint areas that need improvement.
- Why is DAST Important for Application Security?
- How Does DAST Work?
- 6 Pros of DAST
- 4 Cons of DAST
- What Is the Difference Between DAST, SAST, IAST and SCA?
- Top DAST Tools
- Bottom Line: Dynamic Application Security Testing (DAST)
Why is DAST Important for Application Security?
As cyber attacks grow increasingly sophisticated, DAST has become essential for maintaining web application security. It simulates real-world hacking efforts and assists in identifying flaws and vulnerabilities. This helps enterprises to address possible risks before they can be exploited by proactively assessing the application’s security and improving code and overall security posture to protect critical data.
Regular DAST assessments help businesses stay one step ahead of potential risks and contribute to the continual development of secure applications. Enterprises can ensure a stable and resilient environment for their users and stakeholders by continuously evaluating and enhancing their web application security.
How Does DAST Work?
DAST works by simulating the activities of hackers and scanning for vulnerabilities to find potential attack paths and make web applications as secure as possible. By pretending to be a hacker and scanning web applications and emulating hacking techniques, an enterprise’s security team can find the holes and vulnerabilities that might otherwise be used in a cyber attack. The security team examines the application from the outside, attempting to exploit vulnerabilities and assessing the effectiveness of defensive measures. DAST tools employ various techniques such as injection attacks, cross-site scripting (XSS) attempts, and other common attack vectors to identify potential weaknesses.
Security testers can use vulnerability scanning, pentesting and code security tools to help them test the application’s security.
See the Top Application Security Tools & Software
6 Pros of DAST
DAST plays an important role in ensuring the security of web applications, where vulnerabilities can expose critical data to the internet. Here are some of the pros and benefits of DAST security practices.
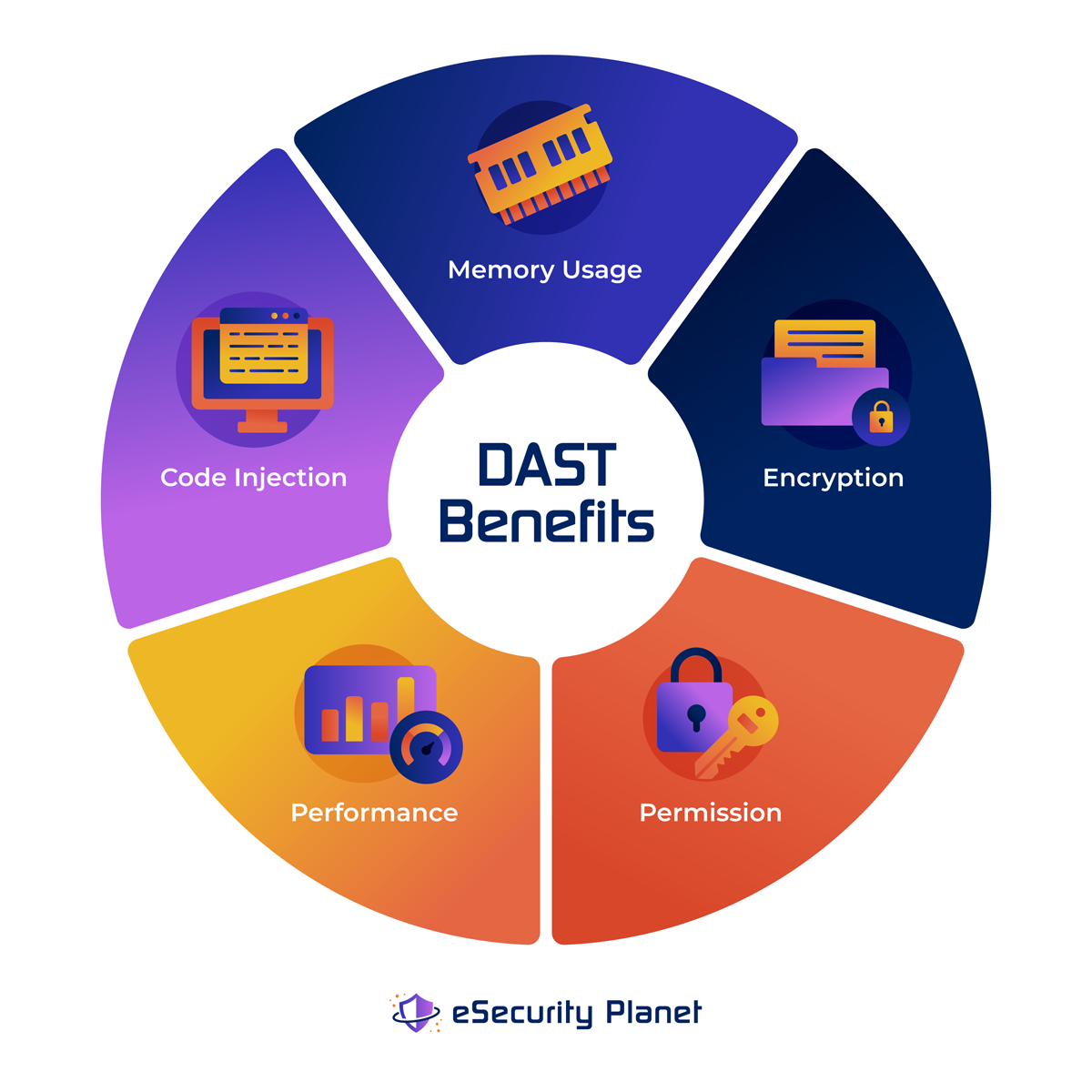
- Real-world simulation: DAST mimics actual hacking techniques, providing a realistic assessment of application security.
- Comprehensive coverage: DAST tests the entire application, including complex interactions, APIs (application programming interfaces), and integrations, ensuring a thorough security assessment.
- Rapid identification of vulnerabilities: DAST tools and solutions can quickly pinpoint exactly where potential security flaws are. This allows for immediate remediation and reduces the window of exposure.
- Lower rate of false alerts: By minimizing the occurrence of false alarms, DAST provides more precise and reliable results, reducing the number of false positives.
- Compatibility with diverse programming languages: With its ability to seamlessly assess the security of web applications developed in a range of programming languages, DAST offers flexibility and effectiveness across different programming frameworks.
- Rapid reevaluation of patched vulnerabilities: Through quick reassessment of resolved vulnerabilities, DAST allows organizations to promptly validate the effectiveness of their patches and ensure that they are no longer exploitable.
See the Best Patch Management Software & Tools
4 Cons of DAST
Despite the benefits, DAST isn’t without costs or limitations. Here are four to consider.
- Limited visibility into source code: Since the external attack nature of DAST restricts its ability to thoroughly analyze the source code, it might potentially miss certain vulnerabilities that require access to the code for detection.
- Impact on application performance: The scanning process of DAST tools can occasionally strain an application’s resources, leading to a potential performance degradation during the testing phase. For critically important applications, this is no small issue, and testing should be done during off-peak hours if possible.
- Delayed CI/CD pipeline results: DAST assessments may introduce delays in the continuous integration/continuous deployment (CI/CD) pipeline, potentially impeding the timely release of application updates or features.
- Potential need for manual testing: DAST scans may generate false positives or miss certain vulnerabilities, which will require additional manual verification to ensure accurate results and avoid overlooking potential security risks.
DAST, SAST, IAST and SCA: What Are the Differences?
DAST and SAST (static application security testing) are complementary methods of application security testing. SAST looks at the program’s source code to find possible security weaknesses before deployment, whereas DAST focuses on external analysis of the application and attempts to attack vulnerabilities in real-time.
While SAST offers insights on the design and organization of the code, DAST assesses the behavior of the program during runtime. Organizations frequently utilize a mix of the two approaches, each of which has advantages and disadvantages, to provide full security coverage.
Interactive application security testing (IAST) combines both DAST and SAST approaches, while software composition analysis (SCA) can also address configuration issues with applications that can potentially be exploited. There are also software dependencies and libraries that have known vulnerabilities, which is where vulnerability management capabilities fit in.
See the Top Vulnerability Management Tools
Top 3 DAST Tools

Invicti
Invicti, formerly known as Netsparker, is renowned for its advanced scanning technology and comprehensive coverage. It offers accurate detection of vulnerabilities, including complicated issues, and provides detailed reports for immediate and efficient remediation. It has a user-friendly interface and robust automation capabilities, making it one of the most popular choices among security professionals.

Veracode
Veracode is recognized for its comprehensive application security platform, which includes dynamic scanning capabilities. It combines DAST with static analysis (SAST) and software composition analysis (SCA) to provide a holistic approach to application security. Veracode’s industry-leading accuracy, scalability, and integration capabilities make it a preferred choice for organizations seeking end-to-end security testing solutions.

Acunetix
What makes Acunetix stand out is its powerful scanning engine and comprehensive vulnerability detection. It offers a wide range of automated security tests, including DAST, to identify common and advanced web application vulnerabilities. Its intuitive interface, robust reporting features, and extensive checks make it one of the top choices for enterprises seeking for effective web application security testing.
Also read:
Bottom Line: Dynamic Application Security Testing (DAST)
Maintaining web application security in today’s dynamic threat environment requires equally dynamic security approaches, so an enterprise’s web application security strategy must incorporate DAST techniques. DAST offers a realistic and thorough evaluation of application security by simulating actual hacking attempts, enabling enterprises to proactively detect weaknesses. Enterprises can make their application security coverage even more complete by integrating DAST with other security testing methodologies like SAST.
There are DAST products that are readily available that come with powerful scanning methods, precise vulnerability identification, and user-friendly interfaces. Invicti, Veracode, and Acunetix are a few of DAST solutions to consider, but code and application security tools are always evolving and other options exist too.
Adding DAST to an organization’s security plan will improve security posture, safeguard important data, and provide a secure environment for users and stakeholders.
Read next: Top Web Application Firewall (WAF) Solutions
The post What is Dynamic Application Security Testing (DAST)? appeared first on eSecurityPlanet.
]]>The post Top 5 Application Security Tools & Software for 2023 appeared first on eSecurityPlanet.
]]>These tools play a vital role in ensuring the security, integrity, and confidentiality of sensitive information, such as personal data and financial records. By employing application security tools, organizations can proactively identify and address potential security flaws, reducing the risk of exploitation and minimizing the impact of security incidents.
Here we’ll take an in-depth look at five of the top application security tools, followed by features buyers should look for and an examination of different approaches to application and code security.
Also read: Application Security: Complete Definition, Types & Solutions
- GitGuardian Internal Monitoring: Best for dedicated secrets scanning
- Veracode: Best for programming language support
- GitLab: Best for DevOps
- Qualys Cloud Platform: Best for vulnerability management
- Trend Micro Cloud App Security: Best for SaaS protection
- Other Application Security Vendors to Consider
- Key Features of AppSec Software
- Code Analysis and Testing Types
- AppSec vs DevSecOps
- How We Evaluated Application Security Software
- Bottom Line: Application Security Tools
| Application security tool | Key feature | Price | Best for |
|---|---|---|---|
| GitGuardian Internal Monitoring | Real-time automated public and private repositories monitoring | FreeBusiness: $477 to $3667Enterprise: Custom quotes | Dedicated secrets scanning |
| Veracode | Static, dynamic, and software composition analysis | Get a quote from their Contact Us page or visit authorized vendors CDW and AWS. | Programming language support |
| GitLab | Version control system and DevOps platform | FreePremium: $24/user Ultimate: $99/user |
DevOps |
| Qualys Cloud Platform | Vulnerability management | $300 for small businesses to $2,000 for larger packages | Vulnerability management |
| Trend Micro Cloud App Security | SaaS platform protection | Get a quote from Trend Micro’s online calculator found on their website. | SaaS programs |

GitGuardian Internal Monitoring
Best dedicated secrets scanning
GitGuardian, established in 2017, focuses on securing sensitive information and secrets stored in source code repositories. It specializes in detecting and preventing the exposure of API keys, credentials, certificates and other confidential data. It offers real-time scanning, integrations with popular version control systems like GitHub and GitLab, and alerts for potential security breaches related to sensitive data in code.

Key Features
- Real-time automated public and private repositories monitoring
- Internal Git repositories secrets detection
- Detection and remediation alerts
- Developer-driven incident response application
Pros
- Easy installation with a 30-minute quick-start guide
- Streamlined incident resolution and communication
- Focuses on critical issues, reducing remediation effort
- Automatic incident notifications for faster response
- GitHub integration for detecting code secrets and blocking merges
- Offers a free plan
Cons
- User interface could offer better usability and ease of access
- Sensitive data and new repository activities alerts could be better
- Needs more detailed reports with additional metrics and information
Pricing
| FREE | Business | Enterprise |
|---|---|---|
| $0 | $477 – $3667 | Custom Pricing |
| Individual developers and teams of 25 members or fewer | 26 developers to 200 developers | Contact sales team or book a demo |

Veracode
Best for programming language support
Veracode is a comprehensive application security tool that provides static, dynamic, and software composition analysis. It offers a wide range of security testing capabilities, including code scanning, vulnerability assessment, and penetration testing. Veracode supports more than a hundred programming languages and provides detailed reports on security vulnerabilities and weaknesses in applications.
Key Features
- Static Application Security Testing
- Dynamic Application Security Testing
- Software Composition Analysis
- Interactive Application Security Testing
- Security Development Training and eLearning
- Application Security Program Management
- Integrations and APIs
- Reporting and Analytics
Pros
- Accurate vulnerability scanning
- Highlights the risk level and severity of the vulnerabilities
- Comprehensive library of remediation guidance
- Comes with VisualStudio add-on
- Detailed reports on issues and fixes
- Excellent customer service
Cons
- The user interface can be challenging
- Users also report issues with slow performance and false positives
Pricing
Veracode customizes pricing based on the specific needs and features required by each business and does not publish pricing. CDW offers some pricing on Veracode plans and features, while AWS provides pricing for Veracode’s FedRAMP platform. To obtain a quote, contact Veracode’s sales team or visit their Contact Us page. Additionally, you can take advantage of a 14-day free trial.

GitLab
Best DevOps unified platform
GitLab is primarily known as a version control system and DevOps platform but also includes built-in application security features. It offers features like static application testing (SAST), dependency scanning, container scanning, and dynamic application security testing (DAST). GitLab integrates security testing into the development workflow, allowing for continuous security monitoring and mitigation.
Key Features
- Static Application Security Testing
- Dynamic Application Security Testing
- Container Scanning
- Dependency Scanning
- License Scanning
- Coverage-guided Fuzz Testing
- API Security
Pros
- Version/source control
- User-friendly interface
- Streamlined Git CLI integration
- Seamless merge and merge requests
Cons
- Documentation could be more user-friendly and comprehensive
- Integration with third-party software could be better
- Can be challenging to navigate between branches within a repository
- Editing files in a browser can be challenging
- Error messages related to CI/CD could provide more detailed information
Pricing
| Free | Premium | Ultimate |
|---|---|---|
| $0/user | $24/user | $99/user |
| Limited features | Majority of GitLab’s features | All features |

Qualys Cloud Platform
Best for vulnerability management
Qualys is a cloud-based security tool that offers a suite of security and compliance solutions, including application security. It also provides web application scanning and vulnerability management tools. It offers scanning and assessment of web applications to identify vulnerabilities and potential security risks, with detailed reports and remediation. Perhaps more comprehensive than some organizations are looking for, Qualys’ security coverage is as complete as it gets.
Key features
- Continuous monitoring
- Vulnerability management
- Policy compliance
- PCI compliance
- Security assessment questionnaire
- Web application scanning
- Web application firewall
- Global asset view
- Asset management
- API, container and cloud data collection
Pros
- Automated web application scanning
- Automated reporting
- Cloud asset management
- Remediation guidance
- Patching
Cons
- 2FA options could be broader
- Adding domains and networks could be easier
- Discovery and scanning setup could be better integrated
- Module integration could be more seamless
Pricing
Qualys Cloud platform is licensed by customers on an annual basis, and the pricing is determined by factors such as the number of Cloud Platform Apps chosen, IP addresses, web applications and user licenses. Customers have categorized the pricing into three tiers: Express Lite, Express and Enterprise. While Qualys does not publicly disclose its prices, customers have shared that pricing packages can range from $300 for small businesses to $2,000 for larger packages. In addition, Qualys offers a 30-day free trial subscriptions to allow users to test services before committing to a purchase.
See the Top Vulnerability Management Tools

Trend Micro Cloud App Security
Best for SaaS platform protection
Trend Micro Cloud App Security focuses on securing cloud-based applications and services. It provides protection for SaaS platforms like Microsoft 365, Google Workspace, and others. It helps organizations ensure the security and compliance of their cloud-based applications, protecting sensitive data, preventing unauthorized access, and defending against threats.

Key features
- Workload security
- File storage security
- Container security
- Open source security
- Email, ransomware and malware protection
Pros
- Facilitates speedy application deployments
- Real-time protection and immediate blocking of unwanted activities during application runtime
- Prevention of malicious intrusions and protection against hacking or takeovers
- Safeguarding cloud applications from design and deployment issues
Cons
- Web support lacks clarity
- Remote endpoints with weak or intermittent internet connections often appear offline
- Settings are not well organized or clearly defined, requiring significant efforts to locate the desired option for modification
- Occasional false positives
Pricing
Trend Micro offers a user-friendly pricing calculator on its website, giving potential buyers a convenient way of determining an approximate cost tailored to their requirements.
Other Application Security Vendors to Consider
The application security market offers a broad range of tools to meet a variety of needs. Here are an additional seven names to consider, plus our lists of the top DevSecOps, code security, and vulnerability scanning tools.
- Acunetix
- Checkmarx
- Invicti (formerly Netsparker)
- Micro Focus Fortify
- Rapid7
- Snyk
- Synopsys
Also read:
- Top Code Debugging and Code Security Tools
- Best DevSecOps Tools
- Best DevOps, Website, and Application Vulnerability Scanning Tools
- Best Cloud, Container and Data Lake Vulnerability Scanning Tools
- Top Container Security Solutions
Important Features of Application Security Software
Application security tools offer a number of important features that contribute to the overall security posture of applications, protecting against unauthorized access, data breaches, and other security risks.
Authentication: Ensures that users or entities are verified and granted appropriate access based on their identity. It involves verifying credentials such as usernames and passwords, before granting access to applications. The tougher to steal, the better.
Authorization: Determines what actions and resources a user or entity is allowed to access or perform within an application. This enforces access control policies to prevent unauthorized access and restricts privileges based on roles or permissions.
Encryption: This protects sensitive data by converting it into a coded form that can only be accessed or decrypted with the appropriate key. Encryption ensures that data remains confidential and secure, even if intercepted or accessed by unauthorized parties.
Logging: Logs are records of events and activities within an application or resource that helps with monitoring and audits to identify common and unusual patterns of user behavior. Logging captures information about user actions, system events, and security-related incidents, providing a trail of evidence for troubleshooting, compliance, and forensic investigations.
Application security testing: Application security testing refers to the assessment and evaluation of applications for identifying vulnerabilities, weaknesses and security flaws. This includes different types of testing techniques such as static application testing, dynamic application testing, and interactive application security testing (more in the next section).
Auditing and accountability: Audit logs and accountability mechanisms help in compliance with regulations, detecting suspicious behavior and investigating security breaches. This tracks and monitors user activities and security-related incidents to establish accountability and traceability.
Vulnerability scanning: Vulnerability scanning identifies and assesses vulnerabilities within applications, networks, or systems. This allows organizations to proactively address potential security risks. Finding vulnerabilities in the open source dependencies that make up most modern applications is an increasingly critical feature.
Code security review: Code security review is an essential practice that helps identify and remediate potential security weaknesses and ensures applications are built with strong defenses against cyber threats.
WAF integration: Web application firewalls (WAF) are a crucial line of defense for web applications, inspecting traffic, enforcing security policies, and protecting against a wide range of web-based attacks such as SQL injection and cross-site scripting (XSS). Integrating WAFs with application security tools can provide critical information to developers and security teams, helping to protect applications from vulnerabilities until they can be fixed.
SIEM integration: Security information and event management systems (SIEM) collect and analyze security event data from various sources to detect and respond to security incidents. This provides centralized visibility, correlation of events, advanced analytics, and automated alerting, and can help identify application security issues.
Threat intelligence integration: Threat intelligence integrations enhance threat detection and provide real-time insights into emerging threats, including attack techniques and open source vulnerabilities, information that can help both dev and security teams.
Secure development lifecycle (SDL) support: SDL supports the integration of security practices and testing throughout the software development lifecycle, ensuring security is prioritized.
Code Analysis and Testing Types
A key concept to understand in application security is that of the Software Development Lifecycle (SDLC). In that process, there are stages for code development, deployment and ongoing maintenance. As part of that lifecycle there are a number of critical application security approaches.
- Static Analysis: At the foundational level is the security of the application code as it is being developed, which is often an area where static code analysis tools can play a role. This area is called static application security testing, or SAST.
- Dynamic Analysis: For code that is running, dynamic application security testing (DAST) enables the detection of different types of security risks.
- Interactive Application Security Testing: Combining both DAST and SAST approaches is the domain of Interactive Application Security Testing (IAST).
- Software Composition Analysis (SCA): SCA addresses configuration issues, software dependencies and libraries that have known vulnerabilities, important issues in software supply chain security.
Also read: SBOMs: Securing the Software Supply Chain
AppSec vs DevSecOps
An interesting trend in the application security product market is that the many different kinds of tools — application security, code security, debugging, DevSecOps, and vulnerability scanning — have been coming together over time.
DevSecOps tools are perhaps the broadest of these products, encompassing developer tools, container implementation, monitoring tools, and more.
Vulnerability scanning, application security, and DevSecOps increasingly have considerable feature overlap, covering DAST, IAST, SAST, and SCA. There are some noteworthy differences however. DevSecOps tools typically have features for container, Ci/CD, and API management. Fuzzing is more likely to be a feature of vulnerability scanning tools, while AppSec will have a greater focus on Static Code Analysis.
See the Top DevSecOps Tools
How We Evaluated Application Security Software
In our evaluation of application security software, we assessed accuracy and effectiveness, breadth of features, ease of use, integration with development and security tools, automation capabilities, pricing, ideal use cases, and reporting functionality. Detailed reporting and vulnerability prioritization were two important factors, as they give dev and security teams the information they need to make risk-based decisions. Ease of use is generally important in this market, as non-security specialists are critical to the process. Integration capabilities are also crucial for the workflow, so the software should integrate and interact with existing development and security tools.
Bottom Line: Application Security Tools
When selecting an application security tool, it is important to prioritize your organization’s unique requirements and conduct a thorough search before making a purchase decision. To do this, prospective buyers should consider factors such as features and capabilities, supported programming languages, compatibility with existing infrastructure, scalability, ease of use, cost, and the level and quality of technical support provided. Additionally, it is important to involve key stakeholders such as IT security teams and developers in the decision-making process.
An application security tool is critically important for securing applications, the environments they run on, the data they contain, and the employees and customers who depend on them.
Read next: Software Supply Chain Security Guidance for Developers
This updates a November 2020 article by Sean Michael Kerner
The post Top 5 Application Security Tools & Software for 2023 appeared first on eSecurityPlanet.
]]>The post What is Confidential Computing? Definition, Benefits, & Uses appeared first on eSecurityPlanet.
]]>It’s a fast-growing cloud computing technique that has gotten buy-in and support from a variety of hardware, software, and cloud vendors. Read on to learn more about confidential computing, how it works, and how it benefits enterprise data security efforts.
How Does Confidential Computing Work?
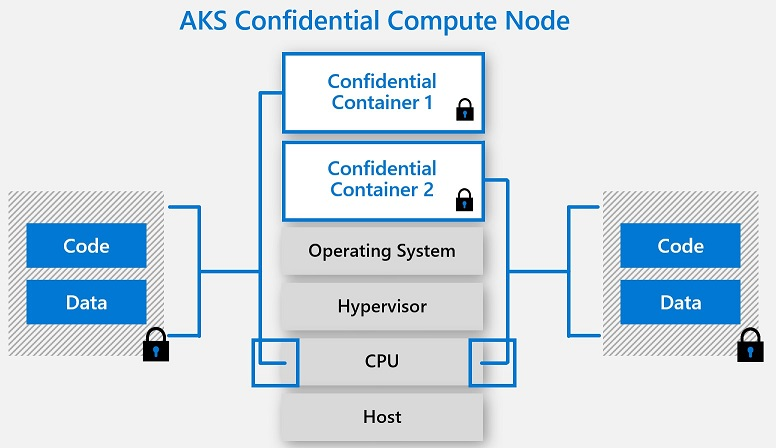
Confidential computing is all about using technology to create an isolated safe space, otherwise known as a Trusted Execution Environment (TEE), for the most sensitive data and data processing instructions. During confidential computing, the TEE and a preselected dataset are separated from the rest of the computing environment, including the operating system, the hypervisor, uninvolved applications, and even cloud service providers.
Unlike other types of data processing, in confidential computing data does not need to be decrypted in memory and exposed to external security vulnerabilities in order to be processed. Instead, it is only decrypted in the Trusted Execution Environment, which relies on hardware-based coprocessor security, embedded encryption keys, and embedded attestation mechanisms to ensure that only authorized applications, users, and programming code can access the TEE and the data it houses. Data processed inside a Trusted Execution Environment is completely invisible to all computing elements that aren’t part of the designated TEE, and data always stays encrypted while in transit or stored outside the TEE.
Also read: Encryption: How It Works, Types, and the Quantum Future
7 Benefits of Using Confidential Computing
Confidential computing offers a number of benefits for safer handling of sensitive data while in use.
1. Added security in shared, untrusted, or unfamiliar environments
The modern computing landscape, especially when the cloud’s involved, means your data is often stored in environments that are exposed to third parties, different departments, and public users. There’s limited native protection built into cloud environments, especially for your most sensitive data when it’s in use. Confidential computing techniques and technologies give your sensitive data more safeguards, regardless of the computing environment.
2. Secure data input and output
The only time data is decrypted during the confidential computing process is when the TEE has taken multiple steps to ensure that only authorized programming code is entering the environment. At all other times, sensitive data remains encrypted, adding more privacy and security while data is in transit or stored in another part of the computing environment.
3. Equal focus on security and cloud computing capabilities
Traditionally, businesses have either had to process sensitive data in memory with major security risks or limit their sensitive data processing in order to protect it; neither approach is ideal for optimal data usability and outcomes. Confidential computing makes it so users can take advantage of the power and complexity of a cloud computing environment while still protecting their sensitive data to the utmost degree.
4. Remote quality assurance capabilities
Confidential computing architecture is designed for remote quality assurance and security management. Remote verification and attestation make it easier for security admins to manage a distributed network while still protecting and monitoring the Trusted Execution Environment.
5. Easier detection and prevention of unauthorized access
Built-in attestation enables the confidential computing architecture to verify programming codes before they can enter the TEE; confidential computing technology can also completely shut down the computing process if an unauthorized set of code attempts to tamper with or gain access to the TEE. This type of computing provides an ideal combination of hands-off security protocols and visibility into unauthorized network traffic.
6. Compatibility with data privacy and compliance requirements
Compliance laws like GDPR and HIPAA require companies to store and use data in specific ways to maintain compliance. It’s not always easy to adhere to these standards in a public cloud environment, but with the additional security features confidential computing provides for sensitive data, businesses can more easily comply with a variety of data privacy and security regulations while still making the most of their data.
7. Protection for data in use
Although other techniques are emerging and being used today, confidential computing is one of the few encryption strategies that effectively protects data in use. Most other encryption approaches protect data at rest and data in transit only.
Also read: Exfiltration Can Be Stopped With Data-in-Use Encryption
Confidential Computing Use Cases
Confidential computing’s protections make it ideal for a number of sensitive data use cases.
Secure third-party outsourcing
Outsourcing certain business functions to third parties is common these days, but it can be a risky move if your data isn’t entirely secure. The enclaved approach taken with TEEs makes it so your internal team can protect and essentially hide sensitive data from unauthorized third-party users, allowing them to focus solely on the parts of your computing process they need to access while trusted members of your team manage sensitive data processes.
Encryption to mitigate insider threats
Because confidential computing means sensitive data is encrypted at all times (until it is processed in the TEE), even members of your internal team cannot access and interpret this protected data without authorization. This feature of confidential computing protects against rogue users within the network as well as users who fall victim to credential phishing attacks.
Protected public cloud use
Businesses are moving many of their workflows and operations to the cloud, but some of the largest enterprises are still hesitant to move their most sensitive workloads to a public cloud environment. With confidential computing in the mix, enterprises can feel more confident and maintain more control over their sensitive data at rest, in transit, and in use, even in a public cloud environment with third-party vendors and users that follow varying security protocols.
See the Best Third-Party Risk Management Software & Tools
IoT data processing
Internet of Things (IoT) devices generate massive amounts of data that are rarely stored in a secure fashion. Confidential computing is increasingly being used to create enclaves where IoT data can be processed in a confidential way that ensures the data isn’t tampered with.
Collaborative data analytics and data usage
Analyzing broader patterns across an organization or an entire industry often requires users to access sensitive data outside of their normal scope of work. Offering an alternative and more secure approach, confidential computing supports secure and collaborative data analytics, allowing users to manage and view their own inputs and gain insights into a sprawling dataset without seeing other users’ inputs or outputs. This approach to analytics is especially helpful in industries like insurance and healthcare where analyzing and interpreting broad patterns can inform insurance rates and diagnostics, respectively.
Blockchain and crypto security
The encryption involved in confidential computing is especially useful in a blockchain environment. Common confidential computing use cases include smart contract, private key, and cryptographic operations management.
Machine learning training
For organizations that want to work with or train a machine learning model without exposing their training dataset, confidential computing is a viable solution for privacy. The machine learning model can be placed in a TEE enclave, allowing data owners and users to share their data with the model and train it in an invisible, isolated environment.
Confidential Computing Consortium (CCC)
The Confidential Computing Consortium (CCC) is a Linux Foundation project community that is made up of various tech leaders. The CCC works to advance confidential computing capabilities and adoption through collaboration on high-profile and open-source confidential computing projects. Its current projects include Enarx, Gramine, Keystone, Occlum, Open Enclave SDK, Veracruz, and Veraison.
The organization is led by two governing officers, a board of directors, committee chairs, and various staff. Members of the Confidential Computing Consortium include Intel, Meta, Microsoft, Google, Accenture, Huawei, Red Hat, Accenture, Anjuna, AMD, Canonical, Cisco, Fortanix, Nvidia, Ruby, and VMware.
Confidential Computing vs. Homomorphic & Data-in-Use Encryption
Confidential computing, fully homomorphic encryption (FHE), and data-in-use encryption share many similarities, especially since they all focus on securing data in use, but each creates a slightly different encryption and usage scenario.
Data-in-use encryption could be looked at as one component of confidential computing; it is used to keep data encrypted until it is in an isolated TEE, where it can then be decrypted by authorized keys and code. Confidential computing also takes this approach to encryption and isolated data processing, but it’s a much broader concept that includes other technologies and strategies, like other types of encryption, secure execution environments and storage, secure communication protocols, and secure key management features.
Fully homomorphic encryption is an old idea that has only recently advanced enough to realize its promise. This approach to data security encrypts data throughout its entire lifecycle, even when it’s being used in computations. Data inputs are encrypted during processing and computing, and results come out encrypted as well. In contrast, both confidential computing and data-in-use encryption allow data to be decrypted and viewed when it’s in the Trusted Execution Environment.
In theory, FHE has some major security benefits since data is encrypted throughout the computing process. However, this type of encryption requires large amounts of overhead, is complex to manage, and has potential for users to make changes to encrypted data without other users ever knowing, thus damaging data integrity. FHE is still early in its development and may overcome some of these shortcomings over time.
Also read: Homomorphic Encryption Makes Real-World Gains, Pushed by Google, IBM, Microsoft
Top 3 Confidential Computing Companies
Confidential computing is a complex process that requires advanced software, hardware, and cloud computing technologies. As such, there are many confidential computing companies and leaders that focus on different parts of the confidential computing architecture. We’ve taken a closer look at three of these leaders below. Other leading confidential computing companies include IBM, Google (Alphabet), AWS, and Fortanix, and promising startups like Anjuna Security, Opaque Systems, Inpher, Gradient Flow, HUB Security, Edgeless Systems, Profian, Secretarium, and Decentriq.

Intel
Intel is one of the first and foremost players in the confidential computing space. Intel Software Guard Extensions (SGX) is the most commonly used hardware-based enclave solution for confidential computing. The company also manages Project Amber, a zero-trust confidential computing project, and Intel Trust Domain Extensions (TDX), a VM-focused approach for added privacy and control. Ron Perez, an Intel fellow and chief security architect at Intel, is the Confidential Computing Consortium’s governing board vice-chair.

Fortanix
Fortanix is considered one of the earliest pioneers in confidential computing. Fortanix’s Confidential Computing Manager (CCM) is a SaaS solution that helps users manage TEEs and protect data in use across various cloud environments. Fortanix is also a founding member of the Confidential Computing Consortium.
Microsoft
Microsoft offers a range of confidential computing solutions primarily through the Azure cloud environment. The Azure confidential computing initiative includes various products and services, such as confidential VMs and confidential VMs with application enclaves, confidential containers, trusted launch, a confidential ledger, SQL Azure Always Encrypted, Microsoft Azure Attestation, and Azure Key Vault M-HSM. Stephen Walli, a principal program manager for Microsoft Azure, is the governing board chair for the Confidential Computing Consortium.
See the Top Enterprise Encryption Products
Bottom Line: Confidential Computing
The modern enterprise network isn’t just an on-premises environment or simple data center. It consists of third-party partners and applications, public and hybrid clouds, and other external factors that feel somewhat beyond the control of traditional network security solutions. Processing data in those environments is more perilous than ever. For companies that want to increase their security and control at the data level, regardless of what their network looks like or who is using it, confidential computing offers a solution to maintain data security while upholding data integrity and enabling high-performance data tasks.
Read next: Security Considerations for Data Lakes
The post What is Confidential Computing? Definition, Benefits, & Uses appeared first on eSecurityPlanet.
]]>The post 10 Best Open-Source Vulnerability Assessment Tools for 2023 appeared first on eSecurityPlanet.
]]>Open source vulnerability testing tools provide cost-effective vulnerability detection solutions. Many IT teams even deploy one or more open source tools in addition to commercial vulnerability scanning tools as backup, or as a check to verify vulnerabilities. In our analysis, here are the best open source vulnerability tools for 2023.
Open Source Website and Application Vulnerability Scanners:
- OSV-Scanner – Best Open Source Code Scanner
- sqlmap – Best for Database Scanning
- Wapiti – Best for SQLi Testing
- ZAP (OWASP Zed Attack Proxy) – Best for XSS Testing
Open Source Infrastructure Vulnerability Scanners:
- CloudSploit – Best Cloud Resource Scanner
- Firmwalker – Best for IoT Scanning
- Nikto2 – Best Web Server Scanner
- OpenSCAP – Best for Compliance-Focused Scanning
- OpenVAS – Best for Endpoint and Network Scanning
- Nmap – Best for Network and Port Scanning
After a discussion of the tools, this article will cover how we evaluated the open source vulnerability scanners and who shouldn’t use an open source vulnerability scanner. For those who might need a refresher on vulnerability scanning, consider reading our guide to vulnerability scanning first.
Open Source Website and Application Vulnerability Scanners
In an ever-connected world, developers continuously churn out complex websites and applications. Website and Application (WebApp) scanners test code in various ways to catch programming errors and vulnerabilities before hackers can locate them.
Most tools will detect common, but critical vulnerabilities listed in the OWASP top 10 such as SQL Injections (SQLi) or Cross-site Scripting (XSS), but may do better in one category than another. Organizations will make their selection based upon deployment flexibility, scanning speed, scanning accuracy, and connections to other tools such as ticketing systems or programming workflow products. However, without licensing costs as a barrier, many teams will deploy several open source tools at the same time.
The following table provides an overview of key tools and capabilities and is followed by an in-depth look at each open source application vulnerability scanner.
| Open Source VulnScan Comparison | XSS Testing | SQLi Testing | Database Scanning | Open Source Code Scanning | Automation Option |
|---|---|---|---|---|---|
| OSV Scanner | n/a | n/a | n/a | Superior | Yes |
| sqlmap | n/a | Superior | Superior | n/a | Yes |
| Wapiti | Good | Superior | n/a | n/a | No |
| ZAP | Superior | Good | n/a | n/a | Yes |
OSV-Scanner
Best open source code scanner
Several other Software Composition Analysis (SCA) tools significantly predate OSV Scanner’s December 13, 2022 launch date and effectively scan static software for open source programming code vulnerabilities. However, the Google-developed OSV pulls from the OSV.dev open source vulnerability database and works in a host of different ecosystems.
While a newcomer, OSV provides a broader range of vulnerability sources and languages and should be considered as either a replacement, or at least a complementary open-source scanning tool for DevOps teams.

Key Features
- Scans software to locate dependencies and the vulnerabilities that affect them
- Stores information about affected versions in JSON, a machine-readable format to integrate with developer packages
- Scans directories, software bill of materials (SBOMs), lockfiles, Debian-based docker images, or software running within Docker containers.
Pros
- Pulls vulnerabilities from a huge number of sources: Apine, Android, crates.io, Debian, Go, Linux, Maven, npm, NuGet, OSS-Fuzz, Packagist, PyPl, RubyGems and more.
- Shows condensed results that reduce time needed for resolution.
- Can ignore vulnerabilities by ID number.
- Still in active development by Google so new features will be added
Cons
- Still in active development, so lacking full features for developer workflow integrations, C/C++ vulnerabilities
- May not yet surpass the specialized capabilities of more focused and older open source SCA tools for their specialty programming languages:
- Bandit: Python
- Brakeman: Ruby on Rails
- VisualCodeGrepper: C, C++, C#, VP, PHP, Java, PL/SQL, Cobol
Sqlmap
Best for database scanning
Some DevOp teams want to scan a back-end database before hooking it up to code. sqlmap enables database vulnerability scanning and penetration testing on a wide variety of databases without distracting the DevOp team with unnecessary features and functions.
Key Features
- Automatically recognizes and uses password hashes
- Developed in Python and can be run on any system with a python interpreter
- Can directly attach to the database for testing via DBMS credentials, IP address, port, and database name
- Full support for more than 35 database management systems including MySQL, Oracle, Postgre SQL, Microsoft SQL Server, IBM DB2, Sybase, SAP MaxDB, Microsoft Access, Amazon Redshift, Apache Ignite, and more.
- Performs six types of SQL Injection techniques: boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries, and out-of-band.
Pros
- Can perform password cracking
- Can search for specific database names and tables
- Supports execution of arbitrary commands and retrieval of standard outputs
Cons
- Command-line tool with no graphic user interface
- Very specialized tool
- Requires expertise in databases to use effectively
Wapiti
Best for SQLi testing
Wapiti performs black-box scans of websites and applications without examining code. Instead, Wapiti uses fuzzing techniques to inject payloads into scripts and check for common vulnerabilities.
Key Features
- Supports GET and POST HTTP methods for attacks
- Modules test for SQL injections (SQLi), XPath Injections, Cross Site Scripting (XSS), file disclosure, Xml eXternal Entity injection (XXE), folder and file enumeration, and more.
- Supports HTTP, HTTPS, and SOCKS5 proxies
- Authentication through Basic, Digest, NTLM or GET/POST on login forms
- Scans can be performed on domains, folders, pages, and URLs.
Pros
- Tests a wide variety of potential vulnerabilities
- Some tests show Wapiti detects more SQLi and Blind SQLi vulnerabilities than other open source tools such as ZAP
Cons
- Command-line tool with no graphic user interface
- Requires significant expertise and knowledge to use
ZAP (OWASP Zed Attack Proxy)
Best for XSS testing
OWASP’s Zed Attack Proxy (ZAP), also available on Kali Linux, places itself between the tester’s browser and the web application to intercept requests, and act as a “proxy,.” This technique allows ZAP to test applications by modifying contents, forwarding packets, and other activities to simulate user and hacker behavior.
Key Features
- Available for major operating systems and Docker
- Docker packaged scans available for quick starts
- Automation framework available
- Comprehensive API available
- Manual and automated exploration available
Pros
- Actively maintained by OWASP teams
- Very comprehensive
- Both graphical and command-line interfaces are available
- Fast learning curve and great documentation
- Convenient for various levels, from beginners to security teams
- Performs very well to detect XSS vulnerabilities
- Can perform fuzzing attacks
- ZAP is commonly used by penetration testers, so using ZAP provides an excellent idea of what vulnerabilities casual attackers might locate
Cons
- Requires additional plugins for some features
- Requires some expertise to use
- Generally produces more false positives than commercial products
Open Source Infrastructure Vulnerability Scanners
Security and IT professionals first developed vulnerability scanners to seek missing patches and misconfigurations in traditional IT networking infrastructure: servers, firewalls, networking equipment, and endpoints. With the increasing complexity of the cloud, virtual machines, and connected devices, vulnerability scanning tools have expanded in number and scope to keep up.
The following table provides a high-level overview of the tools in this category before exploring the tools in depth.
| Open Source IT System VulnScan Comparison | Cloud Resource Scans | Web Server Scans | Endpoint Scans | Network Scans | IoT Scans | Compliance Scans |
|---|---|---|---|---|---|---|
| CloudSploit | Scans AWS, Azure, Google, Oracle | n/a | n/a | n/a | n/a | HIPAA, PCI DSS |
| Firmwalker | Firmware only | n/a | Firmware only | n/a | Firmware Scan | n/a |
| Nikto2 | n/a | Robust variety of scans | n/a | n/a | n/a | n/a |
| OpenSCAP | SCAP policy scan | SCAP policy scan | SCAP policy scan | SCAP policy scan | n/a | Must define compliance in advance |
| OpenVAS | n/a | n/a | Robust variety of scans | n/a | n/a | n/a |
| nmap | Port Scans | Port Scans | Port Scans | Port Scans | n/a | n/a |
CloudSploit
Best cloud resource scanner
Aqua open-sourced the core scanning engine for their CloudSploit so that users can download, modify, and enjoy the benefits of the basic tool. CloudSploit scans can be performed on-demand or configured to run continuously and feed alerts to security and DevOp teams.
Key Features
- Uses RESTful interface for APIs
- API can be called from the command line, scripts, or build systems (Jenkins, CircleCL, AWS CodeBuild, etc.)
- Read/write controls can provide each API key with specific permissions
- Each API call is separately trackable
- Continuous CIS Benchmark auditing for AWS, Azure, and Google Cloud
- Continuous scans can deliver alerts on changes to the cloud infrastructure that introduce vulnerabilities as they occur such as changed security groups, new trusted SSH keys, MFA devices deactivated, deleted logs, and more.
Pros
- Real-time results
- Secure HMAC256 signatures for authentication for API Keys
- Scans for over 95 security risks in seconds
- Intuitive Web GUI
- Supports HIPAA and PCI (DSS) compliance frameworks
- Integrates to send alerts via Slack, Splunk, OpsGenie, Amazon SNS, email, and more.
Cons
- Not available through GitHub
- Automatic update push, some reporting tools, and some integration may only be available with the paid product (additional features are not open source).
Firmwalker
Best for IoT scanning
A few open source teams developed various tools to scan the firmware and settings for network equipment and the internet of things (IoT). Yet, most tend to lean more towards security tools than vulnerability scanners. However, Firmwalker can search through extracted or mounted firmware and report on potential vulnerabilities.
Key Features
- Can search for SSl related files and etc/ssl directories
- Can search for configuration, script, and pin files
- Can recognize and report on keywords such as admin, password, and remote
- Can search for URLs, email addresses and IP addresses
Pros
- Performs a security audit of IoT, networking, OT, and other firmware
- Can locate unexpected files, embedded passwords, or hidden URLs
- Available as a bash script
Cons
- Requires some programming skills to use effectively
- No GUI available
- Shodan API support is currently experimental
Nikto2
Best web server scanner
Nikto2 is an open-source web server scanner that can spot dangerous files and programs as well as server misconfigurations hackers want to exploit. Users can also access Nikto on Kali Linux.
Key Features
- Checks for over 6,700 potentially dangerous files and programs
- Tests for more than 1,250 outdated server versions and 270 version specific problems
- Checks for multiple index files, HTTP server options
- Verifies installed web servers and software
- Can perform credentials guessing
- Techniques available to reduce false-positives
- Outputs to TST, XML, HTML, NBE or CSV file formats
Pros
- Small and lightweight software but still powerful
- Supports files for input and output
- Scan items and plugins are frequently updated but update automatically
- Detects and flags many common issues with web servers
- SSL support for Unix and Windows OS, HTTP Proxy Support
- Option to deploy encoding techniques for intrusion detection system (IDS) evasion and testing
Cons
- No interface, only command lines
- Very specific, which can be confusing for beginners
- Searches are more limited than some commercial tools
- Thorough scans can take more than 45 minutes to complete
OpenSCAP
Best for compliance-focused scanning
OpenSCAP is an open-source framework for Linux platform based on the Security Content Automation Protocol (SCAP) maintained by the US National Institute of Standards and Technology (NIST). The OpenSCAP project creates open-source tools for implementing and enforcing this open standard used to enumerate flaws and misconfigurations.
The scanner provides an extensive range of tools that support scanning on web applications, network infrastructure, databases, and hosts. Unlike most scanners that test for Common Vulnerabilities and Exposures (CVEs), OpenSCAP tests the device against the SCAP standard.
Key Features
- Performs vulnerability assessments on systems
- Accesses public databases of vulnerabilities
- The OpenSCAP Base tool provides a NIST-certified command line scanning tool, a graphical user interface (GUI) is available for more ease of use
- The OpenSCAP Daemon can continuously scan infrastructure for SCAP policy compliance
- Other OpenSCAP tools provide desktop scanning, centralized scan results, or compliant computer images
- Integrates with systems management solutions such as Red Hat Satellite 6, RH Access Insights and more
- The Atomic Scan option can scan containers for security vulnerabilities and compliance issues.
Pros
- Quick identification of security issues and instant corrective operations
- Supported by Red Hat and other open-source vendors
- Combines security vulnerability and compliance scanning
- Can scan docker container images
Cons
- Significantly harder to learn than many other tools
- The multiple tools in the OpenSCAP system can be confusing
- Users need to know the security policy that matches their needs
- Many tools only run on Linux, and some some tools only run on specific Linux distributions
OpenVAS
Best for endpoint and network scanning
Developers created OpenVAS as a multi-purpose scanner by using the last available open source code for Nessus, now a market-leading commercial product released by Tenable. OpenVAS maintains high capabilities to perform large-scale assessments and network vulnerability tests on traditional endpoints and networks. The tool collects insights from a massive range of sources and an extensive database of vulnerabilities.
Key Features
- Scans systems for known vulnerabilities and missing patches
- Web-based management console
- Can be installed on any local or cloud-based machine
- Provides insights on each vulnerability such as how to eliminate the vulnerability or how attackers might exploit the vulnerability
Pros
- Actively maintained by Greenbone
- Covers many CVEs (common vulnerabilities and exposures)
- The scan database is updated regularly
- Large community for peer support
- Organizations that outgrow the Community Edition can upgrade to the Greenbone Enterprise Appliance or Greenbone Cloud Service.
Cons
- Can be overwhelming for beginners and requires some expertise
- Large numbers of concurrent scans can crash the program
- No policy management
- Greenbone Community Edition only scans basic endpoint assets, or Home Application Products, such as Ubuntu Linux, MS Office, etc.
- To scan enterprise products or obtain access to Policies, organizations need to upgrade to the for-pay Greenbone Enterprise version.
Nmap
Best for network and port scanning
The Nmap Security Scanner supports binary packages for Windows, macOS, and Linux and is included in many Linux builds. Nmap uses IP packets to scan device ports and determine what hosts, services, and operating systems are available from the asset under inspection. Penetration testers and IT teams value nmap as a quick, effective, and light-weight tool to list open ports on a system.
Key Features
- Host discovery quickly determines IP addresses up and available on a network.
- Uses TCP/IP stack characteristics to guess device operating systems
- Growing library of 500 scripts for enhanced network discovery and vulnerability assessment
Pros
- Quickly scans open ports on a system and determines available TCP/UDP services
- Interrogates ports to determine running protocols, applications and version numbers
- Large user base and open source community
Cons
- No formal support for customers
- Requires some expertise and IT knowledge to use effectively
Also Read: Nmap Vulnerability Scanning Made Easy: Tutorial
How We Evaluated Open Source Vulnerability Scanners
The staff at eSecurity Planet researched a variety of open source vulnerability scanning tools for this article. We used content from community forums, tool websites, and other resources to obtain industry feedback on the tools.
To be included, tools needed to be primarily vulnerability scanning tools so penetration testing or security tools (endpoint, network, etc.) that merely include a vulnerability scanning function were not generally included. We assume readers are looking for specific tools for vulnerability scanning and we have published other articles on those topics.
Also, the open-source project needed to be updated relatively recently to demonstrate that the tool is keeping pace with the discovery of vulnerabilities. Many popular open source tools such as Arachni, Lynis, Vega, and w3af could not be included because they have not been updated in several years.
Where possible, a winner was selected for a category. However, if a winner could not be selected and another tool on our recommended list could perform some of the functions, then we dropped the category.
For example, many developers created open source container-vulnerability scanning tools such as Anchore, Clair, Dagda, and Trivy. While reviews cite effective results, they also cite significant missing features and difficulty with use or integration. Since OpenSCAP and OSV-Scanner both have some ability to scan containers, we dropped an exclusive container vulnerability scanning tool category for this year.
Who Shouldn’t Use an Open Source Vulnerability Scanner?
Open Source tools can often be downloaded, modified, and used for free. So why shouldn’t everyone use them?
Open source scanners tend to require more technical expertise, more time, and more effort from the IT team members using the tool. Even organizations with expertise in-house often purchase commercial vulnerability scanning tools or vulnerability-management-as-a-service (VMaaS) instead to save time and the hidden labor costs.
1 Intruder
Intruder is the top-rated vulnerability scanner. It saves you time by helping prioritize the most critical vulnerabilities, to avoid exposing your systems. Intruder has direct integrations with cloud providers and runs thousands of thorough checks. It will proactively scan your systems for new threats, such as Spring4Shell, giving you peace of mind. Intruder makes it easy to find and fix issues such as misconfigurations, missing patches, application bugs, and more. Try a 14-day free trial.
In general open source tools will not have the same features, integrations, and capabilities of commercial tools. Open source tools will also lack formal technical support, but some consultants and for-profit companies, such as Greenbone for OpenVAS, provide service and support for a fee. Open source tools may have robust communities available for peer-to-peer support, but the response time to questions can vary and there is no guarantee of helpful responses.
Open source tools also generally rely upon open source databases. This might mean that these tools lag behind commercial tools that have employees dedicated to updating vulnerability databases and in-house research. However, researchers often contribute vulnerabilities to these databases as well, so there are some open source tools that lag only the most aggressively updated commercial tools.
An issue not exclusive to Open Source is that most open source projects rely upon open source building blocks in their development. Contributors regularly police the libraries and work to eliminate vulnerabilities in the code as they are discovered in the software bill of materials (SBOM). However, whether commercial software may or may not be more aggressive than open source teams in closing off potential vulnerabilities needs to be evaluated on a case-by-case basis.
Can Penetration Testing Tools Be Used for Vulnerability Scans?
Many blogs and lists of open source vulnerability scanning tools include a variety of penetration testing tools such as: Wireshark, Metasploit, and Aircrack-Ng. While penetration testing tools can be used to locate vulnerabilities, most of these tools have not been designed to integrate with ticketing systems, provide any ranking or prioritization of vulnerabilities, or incorporate the likelihood of exploitation.
Penetration testing tools work great, but were designed for a different purpose. Engineers and technicians that use penetration testing tools for vulnerability assessments do so more out of habit and comfort level than because they are efficient vulnerability scanning tools.
Also read:
- 10 Top Open Source Penetration Testing Tools
- Penetration Testing vs. Vulnerability Testing: An Important Difference
Bottom Line: Open Source Vulnerability Scanners
The most important step in vulnerability management is to start. Whether or not an organization chooses open source or commercial tools will depend upon their resources and preferences, but the tools should be deployed and used regularly. Regular use of vulnerability scanning tools can detect issues before attackers and give internal teams the time to remediate the issues.
Fortunately, the low cost of open source tools allows for IT, security, and DevOps teams to deploy multiple open source tools even if they also use commercial tools. Hackers often use open source tools to scan systems and software for exploitation, so periodically using these open source tools provides insight into a hacker’s viewpoint and priorities. Even though these tools can demand more effort and expertise, open source vulnerability tools provide a valuable resource to any organization that can effectively use them.
Julien Maury contributed to this report.
The post 10 Best Open-Source Vulnerability Assessment Tools for 2023 appeared first on eSecurityPlanet.
]]>The post What Is a Passkey? The Future of Passwordless Authentication appeared first on eSecurityPlanet.
]]>Passkeys are a lot easier to manage and are resistant to phishing, harvesting and other credential attacks, which is why it’s making its way into the mainstream as a more secure and convenient authentication method. Just last week, Google announced that it will support passkeys for Google accounts.
With passkeys, there is no need to remember complex passwords that are difficult to type and can be easily forgotten. They are also more secure than passwords because they require physical presence or knowledge of the user’s device, making them much harder to hack. There are a number of authentication scenarios where passkeys can be used, including mobile devices, computers, and online accounts.
How Passkeys Work
Passkeys work by using biometric authentication or a unique code to authenticate a user’s identity. There are different types of passkeys, including fingerprint recognition, face recognition, iris recognition, voice recognition, and screen lock pins.
Here’s a brief overview of how each of these passkey approaches works.
1. Fingerprint Recognition
Fingerprint recognition uses a device’s biometric sensor to capture the unique patterns of a person’s fingerprints. When a user places their finger on the sensor, the device compares the captured image with the stored image on the sensor, comparing the captured image with the stored fingerprint data to verify the user’s identity. This passkey is a popular and reliable method because fingerprints are unique to each individual and it is difficult to fake or imitate.
2. Face Recognition
Facial recognition uses the device’s front-facing camera to capture a person’s face and match it against the stored facial data. This type of passkey uses algorithms to identify specific features of the face such as distance between the eyes and the shape of the jawline. It is is convenient and easy to use but it may not be as accurate as other methods especially in a low light or with changes in appearance such as facial hair or makeup.
See the Best Facial Recognition Software for Enterprises
3. Iris Recognition
This kind of passkey uses the device’s camera to capture the unique patterns of a person’s iris, the colored part of the eye surrounding the pupil. Iris recognition technology is very accurate and difficult to spoof because the patterns of the iris are complex and distinctive. Although this method is highly secure and effective, it requires a high-quality camera and may not be as convenient as other methods.
4. Voice Recognition
Voice recognition uses the device’s microphone to capture a person’s voice and match it against stored voice data. This passkey method analyzes different vocal factors such as pitch, tone, and accent to identify the user’s voice. It is convenient and can be used in situations where other methods may not work, such as when the user’s hands are occupied. Even though this passkey is convenient, it may not be as secure as other methods because voices can be spoofed by using recordings, impersonations, and vocal sound manipulation technologies — particularly as AI capabilities continue to improve.
Also read: ChatGPT Security and Privacy Issues Remain in GPT-4
5. Screen Lock Pin
Screen lock pins use a unique code such as a PIN, pattern or mobile password to authenticate the user’s identity. The user must enter the correct code or pattern to unlock the device or website. Screen lock pins are easy to use and can be very secure if the user chooses a strong code. While screen lock pins are convenient and easy to use, they may be vulnerable to attacks such as keylogging, where hackers capture the user’s keystrokes to learn the code.
6 Benefits of Passkeys
As a passwordless authentication solution, passkeys offer a range of benefits that traditional passwords cannot match. From improved security to reduced password fatigue, passkeys could eliminate many of the problems with passwords and transform the way users log in into their accounts and interact with websites and applications. Here are six benefits of passkeys.
1. Increased security
Phishing attacks are a common type of cyber attack where hackers use fake emails or websites to trick users into giving away their login credentials. With passwords, users may be more vulnerable to these attacks because they are required to enter their password on a website or in an email, which can be easily intercepted or stolen. Passkeys provide an effective solution to this problem by eliminating the need for users to enter their passwords.
Learn more about Social Engineering Attacks
2. Convenience
Passkeys are a lot easier to manage and faster to use compared to passwords. Users don’t need to remember complicated passwords and they can access their accounts quickly and easily with a single touch or look. This can save time and frustration, especially when users regularly change passwords and access multiple accounts.
3. Reduced password fatigue
Password fatigue is the feeling of frustration that comes from having to remember multiple complex passwords (or having to reset them when they’ve been forgotten). Passkeys can reduce password fatigue since users only need to remember one passkey method to access all their accounts. And the seamless approach of passkeys can improve employee productivity too, with no need for multiple passwords across accounts.
Also see the Top Single Sign-On (SSO) Solutions
4. Lower risk of data breaches
Passkeys can help decrease the risk of data breaches because they eliminate the need for passwords, often the weakest link in a security system. Passwords can be easily guessed or stolen and even found on the Dark Web, but passkeys are much harder to crack. By using passkeys in business, companies can protect their users’ personal information and prevent sensitive data from falling into the wrong hands.
5. Better user experience
Aside from enhancing the security of user accounts, passkeys also offer a superior user experience compared to traditional passwords. The seamless user experience can greatly improve customer satisfaction and help businesses retain customers. The simplicity of passkeys can even increase brand loyalty among users. By providing hassle-free login processes, any business can increase brand loyalty and establish a more positive and memorable user experience.
6. Reduced costs
Traditional passwords may require businesses to spend considerable resources on password resets, account lockouts and support calls. These issues can be time-consuming and frustrating for users and help desk staff and costly for businesses. Passkeys require less maintenance and support since they utilize biometric data or unique codes. This means that businesses can reduce the amount of time and resources spent on password related issues and put those efforts to better strategic use.
Also Read: Multi-Factor Authentication (MFA) Best Practices & Solutions
How to Create a Passkey
Creating a passkey is a straightforward process that involves determining the passkey type, setting it up on your device, testing the passkey, and using it to access your accounts. Here are four simple steps for creating a passkey for a more secure and convenient way to authenticate identity and protect sensitive information:
1. Determine the type of passkey you want to use
The first step in creating a passkey is to determine the type of passkey you want to use. There are several types available, including fingerprint recognition, face recognition, iris recognition, voice recognition, screen lock pin, or even smartcards. Choose the one that offers the best combination of security and convenience for the information you are trying to protect.
2. Set up the passkey on your device
Once you have determined the type of passkey you want to use, the next step is to set it up on your device. Depending on the passkey type, you may need to enroll your biometric data or set up a unique code. If you are using fingerprint recognition, for example, you will need to enroll your fingerprints on your device. And if you are using a screen lock pin, you will need to create a unique code that only you know.
3. Test the passkey
After you have set up your passkey, it’s important to test it and ensure that it is working correctly. You should try accessing your device or account using your passkey and verify that you are granted access.
4. Use the passkey to access your accounts
Once you have set up and tested your passkey, you can use it to access your accounts. Simply follow the prompts on your device, or the website or application you are trying to access to authenticate your identity using your passkey.
Logging In to Websites & Applications Using Passkeys
Logging into your online accounts can be a hassle, especially if you have to remember multiple login user credentials with multiple complex passwords — or repeatedly sign into a password manager that contains all your passwords. Passkeys will provide you a more convenient and secure alternative. You can use different methods to authenticate your identity that are faster, easier and more repeatable than typing a password. This not only saves time, but also enhances user experience.
See the Best Password Managers for Business & Enterprises
Passkeys vs Passwords
Passkeys and passwords are significantly different methods of authentication for accessing websites and applications.
Passwords are a string of characters, typically a combination of letters, numbers and symbols, that are used to authenticate a user’s identity. Passkeys, on the other hand, use unique biometric data or a unique code to authenticate a user’s identity. Passkeys are more secure than passwords because they are more difficult to replicate, making it harder for hackers to gain access to user accounts.
Passkeys are generally considered more convenient than passwords because they do not require users to remember a complex string of characters. They offer increased security and convenience compared to passwords.
Passkeys vs Passwordless
Passkeys and passwordless essentially mean the same thing – they provide a convenient and secure way to access digital platforms and services without needing to manage cumbersome passwords. Unlike traditional password-based logins, passkeys eliminate the need for users to remember complex passwords or go through the process of entering them each time they want access to their accounts. Passkeys utilize advanced authentication methods, such as biometrics or hardware-based security tokens, to verify the user’s identity. One of the primary advantages of passkeys is their convenience, as users no longer need to create and remember multiple passwords for different accounts. Passwordless approaches also offer improved security, as traditional passwords are susceptible to various attacks.
Top Passkey Solutions
Passkeys are typically based on authentication standards and protocols developed by the FIDO Alliance and the World Wide Web Consortium (W3C), including an API called Web Authentication, or WebAuthn, jointly developed by W3C and FIDO. The FIDO Alliance boasts some of the biggest names in security, authentication, IT, cloud and finance as its members.
Many cloud services providers offer support for passkeys, and organizations looking for a solution for their own security needs could turn to a passwordless authentication or identity and access management vendor that supports a passkey approach.
FIDO has certified hundreds of products as part of the FIDO Certified program. Some of the vendor names include:
- authID
- Aware Inc.
- Beyond Identity
- HYPR
- LoginID
- Ping Identity
- Thales
- Yubico
See the Best Identity and Access Management (IAM) Solutions
Are Passkeys Here to Stay?
It is highly likely that passwordless and passkey authentication are the future, as they offer several advantages over traditional password-based authentication. Passkeys have already gained widespread adoption in the form of biometric authentication on smartphones, and many companies are beginning to explore passkey-based authentication solutions for their websites and applications.
Passkeys have the potential to revolutionize the way we authenticate our identities. By eliminating the need for insecure and difficult-to-manage passwords, passkeys can reduce the risk of data breaches and other cyber attacks. They also provide a more convenient and streamlined authentication for users, which can improve customer satisfaction and retention, not to mention employee compliance with security policies.
Bottom Line: Passkeys
As the world becomes increasingly digitized, the need for secure and reliable authentication grows with it. Passkeys offer a solution that not only improves security, but also provides convenience and simplicity for users. If security isn’t convenient, many users will find ways around it that increase security risks, and that’s a main reason why there’s a strong future for passkeys.
With the ability to authenticate using unique biometric data or codes, passkeys are becoming more prevalent in our daily lives. The adoption of passkeys by major tech companies such as Apple, Microsoft, and Google further validates the importance and potential of this authentication method. It is clear that passkeys are here to stay and have the potential to revolutionize the future of authentication.
Read next: MFA Advantages and Weaknesses
The post What Is a Passkey? The Future of Passwordless Authentication appeared first on eSecurityPlanet.
]]>The post Google Launches Passkeys in Major Push for Passwordless Authentication appeared first on eSecurityPlanet.
]]>In a brief blog post entitled “The beginning of the end of the password,” Google group product manager Christiaan Brand and senior product manager Sriram Karra called passkeys “the easiest and most secure way to sign into apps and websites and a major step toward a ‘passwordless future.'”
Google’s move will make passkeys an additional verification option alongside passwords and two-factor verification. Passkeys can be created within Google accounts at g.co/passkeys.
Passkeys, Brand and Karra wrote, “let users sign into apps and sites the same way they unlock their devices: with a fingerprint, a face scan or a screen lock PIN. And, unlike passwords, passkeys are resistant to online attacks like phishing, making them more secure than things like SMS one-time codes.”
Today’s announcement follows a plan introduced a year ago to implement passwordless support for FIDO Sign-in standards in Android and Chrome, with support from Apple and Microsoft. “Passkeys are a safer, faster, easier replacement for your password,” Microsoft corporate vice president of product management Alex Simons wrote at the time. Microsoft began its own move toward passwordless in Sept. 2021.
As Apple software engineering manager Ricky Mondello put it earlier today, “Step 1: Build everyone’s confidence in passkeys. Step 2: Yeet the password.”
Also read: What Is a Passkey? The Future of Passwordless Authentication
Your Device Is Your Password
In a separate blog post published today, Google’s Arnar Birgisson and Diana K. Smetters explained how passkeys work.
A cryptographic private key is stored on your device, and the corresponding public key is uploaded to Google. “When you sign in, we ask your device to sign a unique challenge with the private key,” Birgisson and Smetters wrote. “Your device only does so if you approve this, which requires unlocking the device. We then verify the signature with your public key.”
It also ensures that the signature can only be shared with Google websites and apps. “This means you don’t have to be as watchful with where you use passkeys as you would with passwords, SMS verification codes, etc.,” Birgisson and Smetters wrote.
“When you use a passkey to sign into your Google Account, it proves to Google that you have access to your device and are able to unlock it,” Birgisson and Smetters wrote. “Together, this means that passkeys protect you against phishing and any accidental mishandling that passwords are prone to, such as being reused or exposed in a data breach.”
Syncing Between Devices
Some platforms can sync passkeys to other devices using end-to-end encryption – a passkey created on an iPhone, for example, can also be accessed on other Apple devices that are signed into the same iCloud account. “This protects you from being locked out of your account in case you lose your devices, and makes it easier for you to upgrade from one device to another,” Birgisson and Smetters wrote.
Still, passkeys do allow anyone with physical access to your unlocked device to access your account. “While that might sound a bit alarming, most people will find it easier to control access to their devices rather than maintaining good security posture with passwords and having to be on constant lookout for phishing attempts,” Birgisson and Smetters wrote.
In the short term at least, some challenges remain. In response to a customer query, 1Password tweeted that “support for passkeys in 1Password isn’t available quite yet but will be coming this summer!” Another user noted that passkeys are not yet supported in Google Workspace, observing, “Workspace admins first have to enable passkeys, but the option is not available yet.”
And using Firefox on a MacBook Air with a fingerprint sensor, my attempt to create a passkey returned a frustratingly straightforward error message: “A passkey can’t be created on this device.” Unsurprisingly, though, it worked using Chrome.
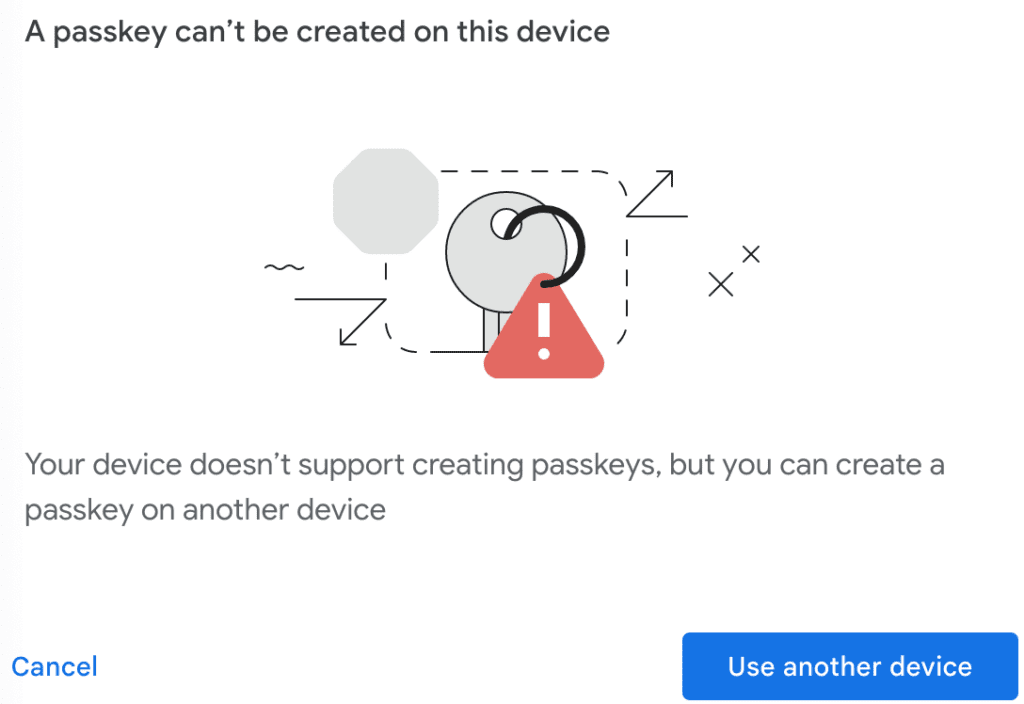
Despite any shortcomings or hiccups, Google’s move is a big move forward for passkeys, and a future without passwords in general.
Read next:
- The Best Password Managers for Business & Enterprises
- Best Identity and Access Management (IAM) Solutions
The post Google Launches Passkeys in Major Push for Passwordless Authentication appeared first on eSecurityPlanet.
]]>The post Automated Patch Management: Definition, Tools & How It Works appeared first on eSecurityPlanet.
]]>Automated patching can save IT and security staff time by deploying the latest security and performance enhancements, fixing bugs, and conducting other upgrades to ensure that software is in its most current state. Automated patch management is a more proactive approach than manual patch management, where critical patches can be delayed or overlooked amid the hundreds of flaws discovered each month.
In this article, we will define automatic patch management, explain how it operates, go through its benefits and drawbacks, and list some of the best practices and top automated patch management tools of 2023.
How Automated Patch Management Works
Patch management is one of the most important aspects of cybersecurity. Software updates are critical for keeping a system’s integrity and security intact. To be effective, patch management should be a consistent and repeatable process of distributing and implementing updates to software and firmware.
A manual or haphazard approach to addressing security and functionality issues can be time-consuming and repetitive and leave significant vulnerabilities exposed. That’s where automated patch management comes in by determining what needs patching and then applying those patches. Here’s how it works.
Network Scanning and Inventory: The initial stage in automated patch management is to find and catalog all network devices, as well as the software programs installed on each device. A discovery tool typically starts this process by scanning the network and generating a list of all the devices and software programs. A vulnerability scanner will look for known security flaws, and some even provide a risk rating to each device and vulnerability.
Assessment: After the inventory has been completed, the patch management tool prioritizes the devices and software that should be patched first based on risk assessment.
Testing and Patch Deployment: Before deployment, patches can be tested to ensure their compatibility with other software on the system. After prioritizing the devices and apps, the patch management program automatically distributes the appropriate patches to each device or program.
Report Generation: After the patches are distributed, the patch management tool creates reports and alerts to inform the administrator of which devices have been successfully patched, which devices still need to be patched, and any difficulties that may have emerged during the patching process.
Monitoring: Once the tool has generated the reports, it then monitors the network to guarantee that all devices are running the most recent patches and upgrades. The tools sometimes include a rollback function in case a patch causes unexpected problems. Problems that can’t be fixed might require manual controls, sometimes called virtual patching.
Also read: Is the Answer to Vulnerabilities Patch Management as a Service?
Pros and Cons of Automated Patching
As with every technology, there are advantages and disadvantages to automated patching, but typically there’s a net benefit.
Automating the entire patching process saves time and work and improves security to an extent that manual patching could never do. This is especially true for enterprises that handle a large number of devices, as manually patching each device might be time-consuming and may require a lot of staff hours and resources. But even overburdened small businesses can benefit from the practice. By ensuring that all devices on the network are up to date with the latest security patches and upgrades, automated patching can lessen the risk of security breaches.
However, one disadvantage of automated patching is that for a large system with many devices, operating systems and applications, it can be difficult to verify that fixes are appropriately applied across all network devices. Also, many larger organizations like to test patches before applying them, so with automated patching they might not know of incompatibility issues until there’s a problem. Fortunately, many automated patch solutions can help test patches before deployment.
And generally, given the cost of data breaches, erring on the side of security is rarely a bad idea.
How to Automate Patch Management
A specialized software program can be used to automate the entire patch management process and give the security team a holistic view of the whole process. Here are the steps for setting up and automated patch management process:
- Installation: The first step of automating patch management is Installing a patch management software solution designed specifically for automating the process of identifying, analyzing, prioritizing, and deploying software patches and updates. There are various patch management tools available on the market, each with somewhat different features and capabilities; we’ll get to those in a moment. Some operating systems, like Windows and macOS, can be set to update automatically, but that won’t cover all firmware and applications on a device.
- Configuration: After installing the patch management program, configure it to operate with your organization’s specific network configuration. This often requires setting the tool to scan the network for devices and software applications, configuring the tool to prioritize which devices and apps need to be patched first, and configuring the tool to distribute patches and updates automatically.
- Scheduling Scans and Deployments: After configuring the patch management tool, the next step is to schedule periodic scans to find new vulnerabilities and distribute fixes and updates to impacted devices and apps. The patch management tool may be configured to scan and deliver patches automatically on a predefined schedule or manually by the administrator. It’s worth noting that cloud services typically patch continuously to stay on top of vulnerabilities; that’s what top security requires.
- Monitoring and Reporting: Once the patch management solution is operational, it is critical to monitor and report on its activities. This involves tracking patches, updating device and application status, providing patch management activity reports, and tracking compliance with industry standards and laws.
Automated Patch Management Best Practices
To get the most out of automated patch management, these best practices should be followed.
- Create a patch management policy outlining the procedures for discovering, testing, and delivering fixes throughout the network.
- Unify software versions and categorize devices according to their software requirements or divisions.
- Scan the network on a regular basis for devices and software that require fixes.
- Conduct tests to check if the strategy is efficient. Before deploying fixes, ensure that there are no compatibility issues or conflicts with other software on the system.
- Apply the patches during non-business hours to minimize user inconvenience.
- Keep meticulous records of all patches applied to the network, all the patched devices, and the method by which these were patched.
- Monitor reports to ensure that the tools function properly.
See our free Patch Management Policy Template
Top 5 Automated Patch Management Tools
These tools are widely considered as among the top options for automated patch management, and have been evaluated by our staff. Considerations such as network size and complexity, device and software types utilized, and an organization’s budget and resources can be factors when selecting an automated patch management tool. Here are some of the top automated patch management tools:

Ivanti Patch Management
Ivanti Patch Management uses an agent-based scanning method to discover and inventory all devices and software applications on a network. Then it assesses the vulnerabilities and risks associated with each device and application, and prioritizes which devices and applications need to be patched first based on their risk rating. After that, it deploys patches and updates automatically, either according to a set schedule or manually triggered by the administrator.
Ivanti Patch Management generates reports and alerts to let the administrator know which devices have been successfully patched, which devices still need to be patched, and any issues that may have arisen during the patching process. The tool also monitors the network to ensure that all devices remain up-to-date with the latest patches and updates.
Pros
- Ivanti Patch Management is a comprehensive patch management system that includes features and capabilities for automating the patch management process such as discovery and inventory, evaluation and prioritizing, patch deployment, and reporting and monitoring.
- Ivanti Patch Management employs agent-based scanning, which provides more accurate and complete information on each device and application on the network.
- To provide a more complete security and management solution, Ivanti Patch Management may be connected with other Ivanti products such as Ivanti Endpoint Manager and Ivanti Security Controls.
Cons
- Complexity: Ivanti Patch Management can be difficult to set up and configure, particularly in big and complicated networks, as it demands a substantial number of resources to implement and administer properly, including hardware, software, and staff.
- Cost: Ivanti Patch Management is a premium tool that might be costly for small and mid-sized businesses.
Pricing
- Prices start at $18.75 per device per year, with bulk savings available for larger enterprises. Flexible pricing options are available based on the number of devices being managed and the level of support required.
Microsoft Configuration Manager
Microsoft Configuration Manager, formerly System Center Configuration Manager (SCCM) and now under the Microsoft Intune brand, is a comprehensive system management tool that is capable of patching Windows devices as well as managing software inventories and configuration settings. For enterprises that employ Microsoft tools and services, Configuration Manager is a common choice.
Configuration Manager discovers and inventories all network devices and software applications using a client-based or agent-based scanning approach. It sends patches and updates to devices automatically or manually, according to a defined schedule or when activated by the administrator. It creates reports and notifies the administrator of which devices have been successfully patched, which devices remain unpatched, and any difficulties that may have emerged during the patching process. The network is also monitored to ensure that all devices remain up-to-date with the latest patches and updates.
Pros
- Configuration Manager integrates well with other Microsoft products, such as Azure Active Directory, for a more comprehensive systems administration solution.
- It supports patching for Windows, macOS, and Linux systems, as well as third-party applications.
- Configuration Manager is adaptable and versatile, with a wide range of configuration choices to meet the needs of each company.
- Configuration Manager provides a variety of functions, including patch management, software deployment, compliance management, and asset management, among others.
Cons
- Complexity: Configuration Manager can be difficult to set up and configure, particularly in big and complicated networks, as it also demands a substantial number of resources to implement and administer properly, including hardware, software, and staff.
- Cost: Configuration Manager is a premium tool that might be costly for small and mid-sized businesses.
Pricing
- Configuration Manager is priced per device or user, with bulk savings offered for bigger deployments. Prices begin at $22 per month per user or $86 per device per year.

Heimdal
Heimdal is a patch management application that assists enterprises in keeping their systems up to date and secure. Some significant features of Heimdal include checking and installing patches and updates to operating systems, software programs, and third-party applications automatically. Heimdal also performs vulnerability scanning to identify potential security problems and provide remedial suggestions. It offers a thorough inventory of installed software, including version information and patch status. It also offers Endpoint Detection and Response (EDR) features to assist in the detection and response to security events.
Pros
- Heimdal offers an intuitive and user-friendly interface that makes patch management and deployment simple for admins.
- Heimdal is available on Windows, macOS, and Linux.
- Heimdal automates patch management, decreasing administrator burden and boosting system security.
- EDR Capabilities: Heimdal offers EDR capabilities, allowing enterprises to notice and respond to security problems more swiftly.
Cons
- Heimdal’s reporting capabilities are minimal, which may make tracking patch management and vulnerability repair efforts difficult for enterprises.
- The patch management options in Heimdal are pre-configured and do not allow for extensive customisation.
- Heimdal’s patch management capabilities are restricted to a small number of third-party applications.
- The vulnerability scanning and EDR modules are priced separately from the patch management module.
Pricing
- Heimdal is licensed per device, with the patch management module starting at $36 per device per year.

SolarWinds Patch Manager
SolarWinds Patch Manager is an automated patch management tool that allows administrators to approve and apply fixes across their networked systems. It integrates well with Microsoft Configuration Manager and other SolarWinds tools for full network management and allows patching for third-party apps such as Adobe, Java, and Chrome, as well as Microsoft products. SolarWinds Patch Manager keeps an inventory of all software and hardware installed on networked computers. It then generates comprehensive reports on patch status, compliance, and vulnerability data.
Pros
- SolarWinds Patch Manager offers an intuitive and user-friendly interface that makes patch management and deployment simple for administrators.
- It allows patching for a large variety of third-party apps, thus decreasing administrator burden.
- It generates detailed reports on patch status, compliance, and vulnerability data.
- It integrates well with other SolarWinds products, including Server & Application Monitor and Network Performance Monitor, to provide a comprehensive IT management solution.
Cons
- Compatibility: SolarWinds Patch Manager only supports Windows-based operating systems.
- Complexity: It requires a high level of technical competence, making it more complicated to set up and configure.
- Cost: Small and medium-sized organizations may find the product’s cost expensive as it is licensed on a per-node basis.
Pricing
- Prices begin at $2,995 for up to 250 nodes. Pricing might vary based on the number of nodes and the amount of support required.

ManageEngine Patch Manager Plus
ManageEngine Patch Manager Plus is a patch management solution that can patch Linux, macOS, Windows, and third-party apps. It can discover vulnerabilities, fix them automatically, and report on compliance.
ManageEngine Patch Manager Plus automates the patching process, allowing administrators to plan and deploy changes across their networked systems. In addition to Windows, Mac and Linux updates, ManageEngine Patch Manager Plus patches third-party programs such as Adobe, Java, and Chrome. It also allows administrators to test patches prior to deployment. It then provides detailed reporting on patch status, compliance, and vulnerability information. It also provides endpoint protection solutions such as antivirus and firewall to help safeguard networked PCs.
Pros
- Patching is offered for a wide variety of operating systems and third-party apps, minimizing administrator burden.
- It offers an intuitive and user-friendly interface that makes patch management and deployment simple for administrators.
- It delivers extensive reporting on patch status, compliance, and vulnerability information.
- To help safeguard networked computers, ManageEngine Patch Manager Plus provides endpoint protection capabilities such as antivirus and firewall.
Cons
- Complexity: Setup and configuration of ManageEngine Patch Manager Plus can be difficult, requiring a high degree of technical experience.
- Cost: It can be quite expensive, especially for small and medium-sized organizations, as it is licensed on a per-node basis.
Pricing
- Prices start at $345 for up to 50 nodes. Pricing depends on the number of nodes and the amount of support required.
Also read:
- Best Patch Management Software & Tools
- Top Vulnerability Management Tools
- Best Patch Management Service Providers
How to Choose an Automated Patch Management Solution
Your needs and budget will ultimately guide you to the automated patch management tool that works best for you and your organization, but some considerations and sources to examine include functionality, operating systems and applications covered, user feedback, and industry and analyst recognition. Here are some things to consider as you make your buying journey.
- Is the product completely automated — or automated enough to meet your needs?
- Is it compatible with the existing systems and software you are using?
- Does it help improve your security posture and protect your users, data, and digital assets?
- Can it create automated reports to keep you up to date on your patching requirements?
- Does it download operating system and third-party fixes automatically?
- Is it up to date with specific information on your endpoints?
- Are the packages pre-built and ready to go?
- Is the product capable of automatically distributing packages in accordance with a simple user-generated policy?
- Is the price reasonable considering the scope and needs of your business?
Bottom Line: Automated Patch Management
Patch management is a critical cybersecurity practice, and an automated patch management solution can help you protect your organization’s data and assets, lower the risk of security breaches, and save time, resources, and effort. With an automated patch management program in place, you can rest easy knowing that all devices on your network are up to date with the latest patches and security upgrades. To get the most out of automated patching, however, it is important to follow best practices and determine which tools are most appropriate for your needs.
Read next: Vulnerability Management as a Service (VMaaS): Ultimate Guide
The post Automated Patch Management: Definition, Tools & How It Works appeared first on eSecurityPlanet.
]]>The post Patch Management vs Vulnerability Management: What’s the Difference? appeared first on eSecurityPlanet.
]]>Patch management is the subset of vulnerability management that applies to third-party vendors and updates third-party systems using vendor-issued patches.
Despite the close relationship between vulnerability and patch management, confusion exists in the marketplace because some marketing tactics blur the definitions and product names to make better matches for a product’s capabilities. This article will provide an overview of the differences between patch management and vulnerability management, and some guidance for getting started on these critical cybersecurity practices.
Table of contents:
- Key Differences: Patch Management vs Vulnerability Management
- What Is Patch Management?
- What Is Vulnerability Management?
- Should Vulnerability and Patch Management Be Used Together?
- How to Pick a Patch Management or Vulnerability Management Solution
- Bottom Line: Make Investments in Patch and Vulnerability Management
Key Differences: Patch Management vs Vulnerability Management
Patch management is a component of good vulnerability management that focuses on known vulnerabilities in 3rd party vendor systems. Third-party vendor systems include Operating Systems (OS), firmware (software installed on hardware), and applications.
Patch management should be considered a minimum capability for any organization, although it can be very difficult to keep up with patches in sprawling environments. Even consumers and less-technical employees understand patch management to some degree since Microsoft (Windows 10+), Apple (iOS, macOS), and Google (Android, Chrome, etc.) push out automatic patches on a regular basis.
Vulnerability management extends beyond known 3rd-party vulnerabilities to include a broader range of issues, including incorrect installations, configuration errors, security gaps, use of obsolete protocols, architecture issues, and other mistakes. Legacy technologies with known vulnerabilities also fall under vulnerability management and, whether formally acknowledged or not, organizations accept the inherent risk of the vulnerable technologies by continuing to use them.
Many vulnerabilities, such as legacy tech, cannot be fixed using patches. Instead, vulnerability management creates, implements, and maintains compensating controls to protect known vulnerabilities. Virtual patching is a form of compensating controls that use Intrusion Prevention System (IPS) capabilities to shield vulnerabilities, but other technologies can also be deployed such as changing firewall rules, adding network segmentation, and whitelisting. Vulnerability management uses periodic, proactive testing to locate new vulnerabilities and continuously tracks older vulnerabilities.
| Key Differences: Patch and Vulnerability Management | ||
|---|---|---|
| Category | Patch Management | Vulnerability Management |
| Scope | 3rd Party Vendor operating systems, software, firmware | All IT systems, configurations, connections, and security controls |
| Frequency | Tends to be monthly, matching Microsoft’s patching schedule | Could be continuous, but should be at least quarterly (or annually for the smallest organizations) |
| Discovery | Primarily through vendor announcements | Primarily through testing and scans |
| Remediation | Download and apply vendor-created patches | Develop fixes of configuration corrections, compensating controls, and additional layers of security |
| Record Keeping & Reporting | Monthly patches applied, devices with failed patches, time to patch | Current prioritized list of vulnerabilities, compensating control status, vulnerability and penetration scan results |
| Required by Compliance? | Yes | Often required |
What Is Patch Management?
Patch management seeks to maintain IT equipment in optimal condition and add features when available through the acquisition, testing, and application of third-party software updates (aka: patches). Patch management provides the process to prioritize, test, and apply patches for optimal IT condition and minimal operations disruption.
Organizations need to ensure that their patch management process includes all of their systems and not just the common Windows and macOS laptops and desktops. Multiple patch management solutions may be required to cover linux servers, network equipment, installed software, and a full range of devices without operating systems belonging to the internet of things (IoT), medical technology (medtech), industrial control systems (ICS), operations technology (OT), or industrial IoT (IIoT).
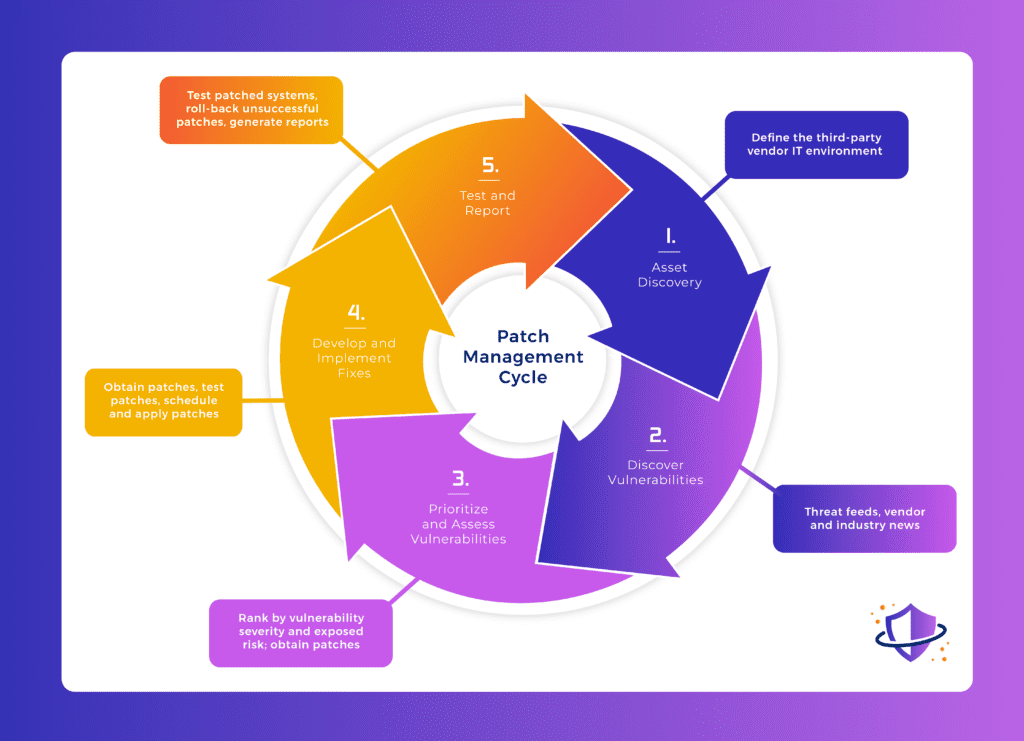
Primary Steps for Patch Management
- Define the IT Environment Through Asset discovery or IT Asset Management (ITAM) to determine endpoints, servers, containers, network equipment, internet of things (IoT), software and other systems to monitor for updates
- Discovery of potential vulnerabilities and available patches through
- Threat feeds
- Vendor emails
- Vendor websites
- Industry websites
- Prioritize and Assess Vulnerabilities
- Prioritize patches based upon severity and the risk to the organization
- Monitor Vendors for the availability of patches to fix vulnerabilities (if no patch is available, engage vulnerability management processes)
- Develop and Implement Fixes
- Acquire patches for updates from legitimate and verified sources
- Test patches and apply test patches
- Assess potential disruptions to operations and notify affected stakeholders in the event of significant disruptions
- Apply patches and monitor for issues
- Test and Report
- Test patched systems to verify proper application of patches
- Roll-back patches in the event of unacceptable disruption, treat as unfixable vulnerability until better patches are released
- Generate reports for internal use and for compliance
See our in-depth guides to Patch Management steps, policies and tools:
- Patch Management Best Practices & Steps
- Patch Management Policy: Steps, Benefits and a Free Template
- Best Patch Management Software & Tools for 2023
- 10 of the Best Patch Management Service Providers
What Is Vulnerability Management?
Similar to patch management, vulnerability management seeks to maintain optimal status for IT equipment, but also extends the principle to all IT systems including network connections, security control systems, and configurations. Vulnerability management requires testing to verify IT system status and to detect configurations errors, security gaps, and other unexpected issues.

Primary Steps for Vulnerability Management
- Define the IT Environment through
- Asset discovery to determine endpoints, servers, containers, network equipment, internet of things (IoT), software and other systems to test and monitor
- Mapping and diagramming network connections, cybersecurity controls, and other systems to test and check
- Discovery of potential vulnerabilities through
- Vulnerability testing and vulnerability scanning (networks, endpoints, cloud systems, containers, applications, etc.)
- Penetration testing
- Threat feeds
- Vendor emails
- Vendor websites
- Industry websites
- Prioritize and Assess Vulnerabilities
- Rank vulnerabilities based upon severity and the risk to the organization
- Which vulnerabilities have patches available
- If no patch is available, which can be corrected with fixes (simple or complex)
- If no patch or fix is available, what compensating controls can be implemented to reduce the risk
- Develop and Implement fixes
- Determine the fix required such as patches, configuration corrections, or compensating controls
- If a fix requires operational disruption, notify affected stakeholders, and schedule downtime
- Implement the fix
- Test and Report
- Test fixes to ensure patches, corrections, or controls were properly installed, no unintended vulnerabilities were created, and the fix works as expected
- Rollback fixes that cause unacceptable operations disruption and go back to development of the fix to try again
- Generate reports for both internal and compliance purposes
For more information on Vulnerability Management consider reading:
- What Is a Vulnerability Assessment? Types, Steps & Benefits
- Penetration Testing vs. Vulnerability Testing: An Important Difference
- 7 Steps of the Vulnerability Assessment Process Explained
- The 8 Best Vulnerability Scanner Tools for 2023
- 12 Top Vulnerability Management Tools for 2023
- Vulnerability Management as a Service (VMaaS): Ultimate Guide
Should Vulnerability and Patch Management Be Used Together?
Many organizations struggle with patch management, so the idea of broadening the requirement to include vulnerability management can be intimidating. However, many vulnerabilities can be easily detected and fixed as long as the organization finds the vulnerability before an attacker can.
Bring-your-own-device (BYOD) adoption helps to illustrate the need for combined use. Consider two laptops, one a corporate device used by a remote worker and the other a consultant’s personal laptop. Both may have an OS vulnerability actively under exploitation, but the patch management tool will only fix the corporate device. The organization will need to use a compensating control, such as network access control (NAC) to detect the unpatched consultant’s laptop and quarantine the device until it is patched.
How to Pick a Patch Management or Vulnerability Management Solution
Patch management tends to be the bare minimum implementation of vulnerability management that an IT team can deploy and still be considered competent. However, just because it needs to be done doesn’t mean all of the pressure and tasks must fall onto an IT or security team.
Automated tools for patch management enable an IT team to let the tool handle the easy updates so the IT team can focus on any problems. Many smaller companies outsource both regular and more difficult patching to managed IT service providers (MSPs).
Organizations looking to improve capabilities to encompass vulnerability management need to carefully evaluate the tools and services under consideration. Many scanning tools, including some labeling themselves as vulnerability management tools, tend to focus primarily on detecting and remediating the unpatched workstations and laptops. While critical, a good vulnerability management solution needs to go further.
Vulnerability management should perform more comprehensive scans of systems, detect misconfigurations, incorporate penetration tests, and other proactive techniques. Some organizations outsource to MSPs, but others prefer to use managed IT security service providers (MSSPs) for their vulnerability management to have a stronger security focus.
Whether outsourcing, selecting a tool, or using inhouse labor, the solution should match the needs. If the service provider or tool only covers Windows and macOS endpoints, the organization will need to find another solution to ensure Linux servers, routers, IoT, and cloud-hosted Kubernetes clusters will be covered.
Organizations need to know the full extent of their needs and the true capabilities of their tools and services to understand what tasks remain unfulfilled. A vulnerability scanning tool or vulnerability management tool that cannot scan for security gaps, open ports, configuration errors, and other non-patching issues will need to be complemented by in-house expertise or consultants that can locate those issues using red teams, penetration tests, and more sophisticated vulnerability scans.
Bottom Line: Make Investments in Patch and Vulnerability Management
Organizations of all sizes should implement the most robust patching or vulnerability management solution their resources allow at the earliest opportunity. Undetected or ignored vulnerabilities will eventually become the target of the increasing volume of cybersecurity attacks. Automated tools and services provide critical help and cost savings by reducing the burden on IT and security teams to manage the easy, repetitive updates. Further investment in expertise to thoroughly test systems and create solutions for the more complex and difficult vulnerabilities will pay off in reduced risk, decreased losses from operations downtime, and less damage from successful attacks.
The post Patch Management vs Vulnerability Management: What’s the Difference? appeared first on eSecurityPlanet.
]]>The post 24 Top Open Source Penetration Testing Tools appeared first on eSecurityPlanet.
]]>Teams often need a variety of tools to perform a full penetration test, so using the wide range of open-source pentesting tools helps them keep their costs down. And many pentesters are already familiar with well known tools like Nmap and Metasploit.
Many of the tools below are included in Kali Linux, a dedicated Linux operating system for pentesting and ethical hacking. Installing Kali can remove the hassle of downloading and installing these tools separately.
The emphasis here is on open-source pentesting tools, so pricing is free but we note where there are paid levels and services too. For commercial pentest tools offering greater breadth and support, see Best Penetration Testing Tools.
Also read:
- What Is Penetration Testing? Complete Guide & Steps
- How to Implement a Penetration Testing Program in 10 Steps
Top Penetration Testing Categories
We have grouped the tools below according to their function in a pentest exercise. Some may fall into multiple categories and there is some overlap between categories, but this list represents our assessment of the major function accomplished by each specific tool. Here are the major categories, which link to the best tools within each category.
- Best web app scanning tools: ZAP, Nikto2, W3af, WPScan
- Best password crackers: John the Ripper, Medusa, Ncrack, Rubeus
- Best pentesting frameworks: Burp, Metasploit, Fiddler
- Best wireless network scanning tools: Hashcat, Aircrack-ng, wifite
- Best exploitation tools: BeEF, SQLmap, SET
- Best sniffing tools: Ettercap, Tcpdump, Wfuzz
- Best network scanners and enumeration tools: Nmap, Wireshark, Gobuster, Amass
4 Best Web App Scanning Tools
These are open-source pentest tools used for testing the security of web-facing applications, servers, and other assets. The top four options include OWASP, Nikto2, W3af, and WPScan.
OWASP
The Open Web Application Security Project (OWASP) maintains Zed Attack Proxy (ZAP), which stands between the tester’s browser and a web application to intercept requests, modify contents, or forward packets, among other tasks.
Pros
- Actively maintained by OWASP teams
- Comprehensive and full of features, such as spider, passive and active scans, application programming interfaces (APIs), request editor, marketplace, plug-ins, and many more
- Supports multiple programming and scripting languages
- Provides graphical and command-line interfaces (CLIs) as well as good documentation
- Convenient for various levels, from beginners to security teams
Cons
- Can be harder to install and less comfortable than premium products such as the Burp Suite
- Needs additional plugins to provide some features
Nikto2
Nikto is a light web server scanner that works with command lines to identify common web flaws, such as server misconfigurations. It can be installed with Kali Linux or as a single package with the command sudo apt install nikto.
It performs tests against multiple items, including thousands of potentially dangerous files and common gateway interfaces (CGIs), and it checks for outdated versions of servers and version-specific problems on hundreds of servers. It also checks for configuration items such as the presence of multiple index files and HTTP server options and will attempt to identify installed web servers and software.
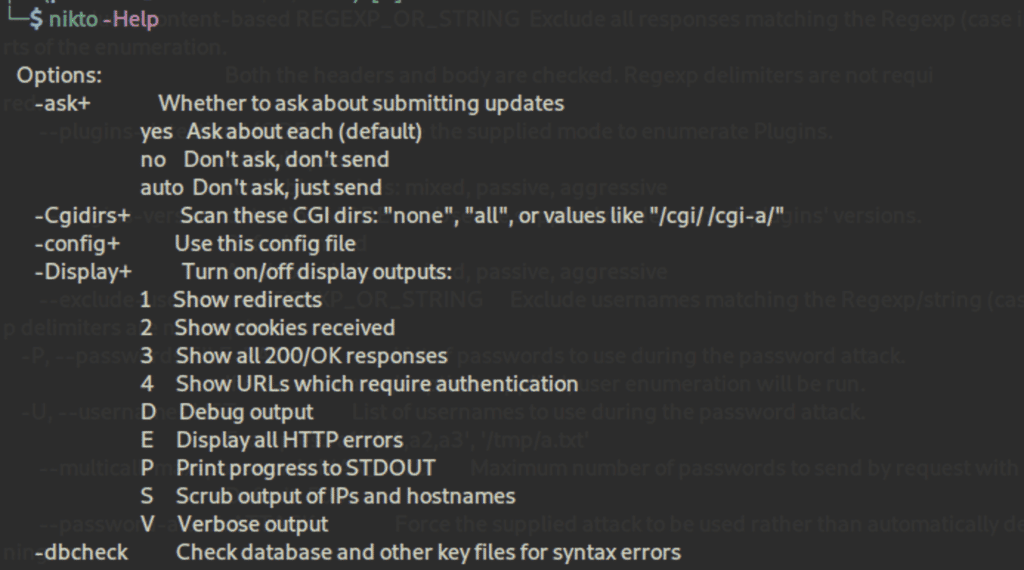
Pros
- Straightforward and covers common needs
- Can test intrusion detection systems (IDS)
- Supports files for input and output
Cons
- Beginners might get confused
- No graphical user interface (GUI)
- No known community or support
W3af
w3af, or Web Application Attack and Audit Framework, is a scanner with a framework to analyze applications and generate reports with its findings. Once the app is mapped, the tool sends crafted requests to trigger specific bugs in the code, such as SQL injections, and to report positive cases.
Pros
- Easy to learn and use
- Generates helpful reports
- Automates many tasks
- Provides a complete documentation
Cons
- The GUI can be challenging
WPScan
WPScan is a popular security tool for WordPress. It can be used with pentesting distributions like Kali Linux, with Docker, or as a binary.
A quick scan can reveal typical flaws of WordPress installations, such as the use of the XML-RPC protocol or outdated dependencies, but it can also perform brute-force attacks efficiently. Behind the scenes, the CLI tool uses the WordPress Vulnerability Database API to retrieve WordPress vulnerability data in real time.
Pros
- Comprehensive with good documentation
- Entirely built for WordPress
Cons
- Free plan has limited API quotas
- A lot of prerequisites if users don’t use Kali Linux
- No GUI
Pricing Upgrades: The CLI tool is free but limited; premium small business and enterprise versions are available.
4 Best Password Crackers
Password cracking consists of retrieving passwords stored in computer systems. System administrators and security teams as well as hackers can use these tools to spot weak passwords. John the Ripper, Medusa, Ncrack, and Rubeus are the top password crackers.
John the Ripper
John the Ripper is one of the most popular free password crackers included in Kali Linux, but it also has a premium version. It combines several approaches to password cracking into one package.
It also supports hundreds of hash and cipher types, including for user passwords of Unix flavors, macOS, Windows, web apps, groupware, database servers, network traffic captures, encrypted private keys, filesystems and disks, archives, and document files.
Pros
- Supports multiple hash and cipher types
- Highly flexible configurations
- Can crack common variations such as mangling rules (e.g., Pa$$w0rd)
- Takes the best aspects of various password crackers and unites them into one package
Cons
- Can be hard to learn, set up, and configure
- Has the same privileges of the user running it, so cannot read shadow passwords
- Only penetrates passwords, nothing else
To learn how to use John the Ripper and hear more about its pros and cons, read John the Ripper: Password Cracking Tutorial and Review.
Medusa
Medusa is a powerful brute-force tool with interesting features included in Kali Linux. This command-line tool can also be installed as a Linux package using the command sudo apt install medusa.
Pros
- Easy to learn and use
- Fast and concurrent
- Supports thread-based parallel testing like simultaneous brute-force attacks
- Offers the ability to resume an interrupted Medusa scan
- Can be extended easily
Cons
- Supports fewer operating systems and platforms than other tools
- Lack of documentation
Ncrack
Ncrack, which is included in Kali Linux, can test all hosts and devices in a network for weak passwords. It’s a set of command lines that can scan large networks, allowing sophisticated brute-force attacks.
Pros
- Light yet powerful
- One of the most widely used by professionals
- Can be easily used along with Nmap and is maintained by the same creators
- Can save output in files
- Can resume an interrupted attackers with the –resume option
- Can attack multiple hosts
Cons
- No graphical interface
Rubeus
Rubeus is a C# toolset for raw Kerberos interaction and abuses. It is open-source and licensed under the BSD 3-Clause license.
It is especially aimed at ever-more popular Kerberos use cases, which is a ticket-based network authentication protocol used in Active Directory (AD) that is commonly misconfigured. Rubeus exploits the resulting vulnerabilities and performs functions such as crafting keys and granting access using forged certificates.
Pros
- Good for Kerberos flaws
- Includes modifications to Rubeus’ approach to Kerberoasting
- Versatile and dropped on the victim’s machine to perform various AD-related attacks
Cons
- Can be detected in a number of methods, either from the host, network, or domain perspectives
- Can be caught during initial weaponization of the code itself through the use of sensitive APIs
For an explanation on how to test your organization’s security services using Rubeus and other pentesting tools, read Testing & Evaluating SIEM Systems: A Review of Rapid7 InsightIDR.
3 Best Pentesting Frameworks
Pentesting frameworks are collections of security tools that can be used to run penetration tests. The best ones, including the Burp Suite, Metasploit, and Fiddler, cover both scanning and exploits.
The Burp Suite
Burp is a top-rated software suite for attacking that can be found in the Kali Linux community edition. It’s a tremendous tool in the pentesting arsenal that can do advanced scans, but one of the most classic uses is traffic interception, such as for HTTP requests.
The web vulnerability scanner within Burp Suite uses research from PortSwigger to help users find a wide range of vulnerabilities in web applications automatically. Burp Scanners crawl engine cuts through obstacles like CSRF tokens, stateful functionality, and overloaded or volatile URLs. It can handle dynamic content, unstable internet connections, API definitions, and web applications.
Pros
- Used by most security teams, researchers, and professionals as well as attackers
- Comprehensive
- Easy to use and configure
- Its embedded Chromium browser renders and crawls JavaScript
- A crawling algorithm builds up a profile of its target in a similar way to a tester
- Uses location fingerprinting techniques to identify hidden areas
Cons
- Harder to learn and master than other scanners
- Many features aren’t available in the community edition (free), and the enterprise edition is relatively expensive
- An all-in-one solution with tons of features that won’t be used by many businesses
- As it tries to be everything, it should be viewed as primarily a vulnerability scanner with some penetration tools that attack the exploits it uncovers. But it should be used in conjunction with other pentesting tools
Pricing Upgrades: In addition to the free community tools, PortSwigger offers pro and enterprise versions of Burp.
Metasploit
Metasploit, developed by Rapid7, is a well-known exploitation framework that’s also included in Kali Linux. It provides useful modules and scanners to exploit vulnerabilities.
With this modular exploitation approach, a particular vulnerability can be combined with a user-selected payload module and an automatically selected encoder module. Upon success, the user can adapt and customize their workflow by using one of the many post-exploitation modules provided by Metasploit Framework.
Further, Metasploit is backed by a huge open-source database of known exploits, and provides IT with an analysis of pentesting results, so remediation steps can be done efficiently.
Pros
- Used by most security teams, researchers, and professionals as well as attackers
- Comprehensive
- Convenient to emulate compromised machines
- Users can create infected payloads with a graphical interface with the payloads GUI or in the pro version
- Can be easily combined with Nmap
- Includes post-exploitation tools such as keyloggers, packets sniffers, or persistent backdoors
- Tests can be automated
- Everything is unified to provide a seamless experience for the user, particularly when compared with stand-alone public proof-of-concept code
- With an established Meterpreter or Secure Shell (SSH) session, users can send all traffic through one or more sessions depending on their Metasploit-global routing configuration
Cons
- It makes hacking a lot easier, including for beginners and script kiddies
- Paid versions are expensive
- Can be challenging to use at first
- May occasionally have scaling challenges in very large environments
Pricing Upgrades: In addition to the open-source framework, Rapid7 also offers a professional version.
Fiddler
Fiddler is a useful collection of manual tools for dealing with web debugging, web session manipulation, and security and performance testing. This includes:
- Watcher to observe browser interactions with a website, scan requests and responses, and flag potential vulnerabilities
- x5s to evaluate website vulnerabilities due to cross-site scripting bugs caused by character-set related issues
- intruder21 for fuzz testing of web applications, generating fuzzed payloads and launching them against a website
- Ammonite, which detects common website vulnerabilities including SQL injection, OS command injection, cross-site scripting, file inclusion, and buffer overflows
Pros
- Good web debugging proxy
- Can automate SSL decryption
- Users can choose to either decrypt all processes, only browser traffic, only non-browser traffic or remote clients
Cons
- Not designed to be a pentest tool but helps to scan for vulnerabilities
- Probably most useful for those deploying the paid version on the .NET framework, as that comes with many automation features
Pricing Upgrades: While Fiddler is free, a paid version by Telerik can be integrated into .NET applications.
3 Best Wireless Network Scanning Tools
Wireless network scanning tools test the security of wireless networks by cracking network passwords and testing the strength of encryption protocols. The top wireless network scanning platforms are Hashcat, Aircrack-ng, and wifite.
Hashcat
Hashcat provides advanced password recovery features and lets testers crack Wi-Fi passwords or password-protected documents such as ZIP files. It’s already included in Kali Linux, but users can install it as a package using the command sudo apt install hashcat.
Pros
- A typical hacker’s tool
- Not limited to brute-force attacks
Cons
- No GUI, but there are third-party integrations
- Requires relatively advanced technical knowledge
Aircrack-ng
Aircrack-ng is the go-to tool for analyzing and cracking wireless networks. All of the various tools within it use a command-line interface and are set up for scripting. Aircrack-ng’s main focuses include:
- Packet capture and export of data to text files for further processing by third-party tools
- Replay attacks, de-authentication, fake access points, and others via packet injection
- Check Wi-Fi cards and driver capabilities (capture and injection)
- Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access Pre-Shared Key (WPA-PSK) for WPA and WPA2 cracking
Pentesters can use it to attack and crack the WPA and WEP protocols. It is open-source and available from SecTools.
Pros
- Good tool for 802.11 wireless local area networks (LANs) to to sniff wireless packets, intercept them, and log traffic passing through, as well as manage wireless drivers and recover lost keys
- Has been extended beyond Linux to include Windows, OS X, FreeBSD, OpenBSD, NetBSD, Solaris, and eComStation 2
Cons
- Cannot monitor or conduct pentesting on non-wireless networks
wifite
Wifite is a wireless network auditor that deals with current or legacy attacks against WEP and WPA2. It can be used as an automated wireless attack tool.
Pros
- Good for retrieving the password of a wireless access point such as a router
Cons
- Mainly designed for use with pentesting distributions of Linux
- Wifite must be run as root by the suite of programs it uses
- Difficult to run downloaded scripts
3 Best Exploitation Tools
Exploitation tools can test everything from user susceptibility to phishing and spoofing to application and database security. BeEF, SQLmap, and SET are the most useful exploitation tools available.
BeEF
As many apps are web-based, adversaries use browser exploitation. BeEF, or Browser Exploitation Framework, makes classic tasks such as enumeration, phishing, or social engineering seamless.
This software provides testers a user-friendly GUI and practical client-side attack vectors to target different contexts and achieve various tasks, such as stealing credentials. BeEF also offers a user guide for anyone with questions from basic utilization to development.
Users can find it in Kali Linux, but it can also be installed as a package using the command sudo apt install beef-xss.

Pros
- Full of advanced features, such as fake password manager logins and redirect with iFrames
- Clever interface to visualize everything from the victim’s browser to the attacker’s logs
- Particularly convenient for demonstrations
- Provides prebuilt web pages for various traps such as fake login forms
- Can bypass a victim’s firewall
- Provides a comprehensive network module, such as for host discovery
Cons
- Basic phishing modules will perform poorly with cybersecurity-aware employees
SQLmap
SQLmap is included in Kali Linux, but it can also be installed from the GitHub repository. It automates the process of detecting and exploiting SQL injection flaws and database server takeovers.
Pros
- Can detect various types of SQL injections
- Supports an extensive range of databases
- Provides advanced features, especially for search and enumeration
Cons
- No GUI; it’s CLI-only, but there are third-party integrations
SET
SET, or Social Engineer Toolkit, focuses on the human factor, as scanners won’t do social engineering pentests. Users will be able to create payloads, phishing pages like Google login, and other web attacks.
Pros
- The sets of command lines, used in place of a GUI, has a nice format
- Comprehensive
- Straightforward but powerful
Cons
- Based on human mistakes, which is often the weakest link, but some attacks don’t need this step
3 Best Sniffing Tools
Packet sniffers can analyze and intercept network traffic to steal data and passwords and launch man-in-the-middle attacks. When searching for a top sniffing tool, consider Ettercap, Tcpdump, and Wfuzz.
Ettercap
Ettercap is a packet sniffer that allows users to modify data on the fly and run man-in-the-middle (MITM) attacks. A common usage is to intercept passwords with ARP (Address Resolution Protocol) poisoning or spoofing, which attackers place between the victim and router to divert the traffic.
Ettercap can be used with Kali Linux or installed as a stand-alone software on a pen-testing distribution using the command sudo apt install ettercap-common.
Pros
- A typical hacker’s tool
- Will put security systems such as EDR (endpoint detection and response) to the test
- GUI and command lines
Cons
- Users need to be already inside the network to run the attack
- The interface could be more polished
- Can be hard to learn and master
Tcpdump
Tcpdump is a powerful command-line packet analyzer developed by the same people as libpcap, a portable C/C++ library for network traffic capture. It prints out a description of the contents of packets on a network interface, preceded by a timestamp.
Pros
- Can save packet data to a file for later analysis
- Reads from a saved packet file rather than reading packets from a network interface
- Can read a list of saved packet files
Cons
- Command line only
- Can impact performance at times
Wfuzz
Wfuzz is helpful to run brute-force attacks on various elements such as directories, scripts, or forms. Like many other tools in our list, it can be found in Kali Linux, but users can run it with the command sudo apt install wfuzz.
Pros
- Accepts wordlists
- Allows customized configurations
- Documented
Cons
- Significantly slower than other options
- Requires more central processing unit (CPU) power and random access memory (RAM)
4 Best Network Scanning and Enumeration Tools
Network scanning and enumeration tools probe networks and traffic for weaknesses and vulnerabilities. Nmap Free Security Scanner, Wireshark, Gobuster Directory Scanner, and Gobuster Directory Scanner are leading network scanning and enumeration tools.
Nmap Free Security Scanner
Nmap, included in Kali Linux and also available via nmap.org, is a free package of command lines that can be run in a terminal to achieve various tasks, such as discovering open ports, which allows users to detect vulnerabilities. This tool is helpful for scanning large networks fast.
Behind the scenes, Nmap uses raw IP packets to identify available hosts and services on the network. As well as a port scanner, it aids pentesting by flagging the best areas to target in an attack, which is useful for ethical hackers in determining network weaknesses.
Pros
- A comprehensive, free, and open-source solution
- Can be combined with a GUI such as Zenmap
- Full of advanced networking features
- Accepts custom scripts
- Can scale to scan huge networks but can also be deployed against single hosts
Cons
- Can be hard to configure and master, especially for those not familiar with Linux; however, it does run on other OSes
- The extensive range of commands and options can overwhelming
- Detection tools will likely spot and log Nmap scans
- Although Nmap is a scanner, it doesn’t probe for and penetrate vulnerabilities though it does point out where weaknesses might lie
Wireshark
Wireshark is probably the most popular network protocol analyzer. It’s a packer scanner, or sniffer, that can be found in Kali Linux, but users can also install it as a stand-alone software or package in most operating systems.
Wireshark is often used to point out what is happening with the network and to assess traffic for vulnerabilities in real time. By reviewing connection-level information as well and the constituents of data packets, it highlights their characteristics, origin, destination, and more.
Pros
- Rich interface with lots of panels and removable tabs
- Can see the finest details
- Assesses traffic vulnerabilities in real time
- Can be used to assess wireless networks
- Runs on Windows, Linux, Mac, and most other OSes
- Output can be exported to XML, PostScript, CSV, or plain text
Cons
- Harder to learn and master than other mappers
- Captures all requests on the network, so you have to know how to fine-tune it and use filters
- While it flags potential weaknesses, a pentesting tool is still required to exploit them
Gobuster Directory Scanner
Gobuster can be used with Kali Linux, but users can also install it as a package using the command sudo apt install gobuster. It is efficient software that can be used to enumerate hidden directories and files quickly.
Many web apps use default directories and filenames that are relatively easy to spot. As a result, the tool can use brute-force techniques to discover them.
Pros
- Accepts Wordlists and additional packages via the command sudo apt install seclists
- Can extract lots of information such as directories, subdomains, and virtual hosts
- Able to hide status and process such as with proxies and user agents
- Spots backup and configuration files
- Can save output results in files
Cons
- Some Gobuster modules have limited options
- Robust installations will likely make enumeration more difficult or perhaps block it
Amass
Amass is an open-source network mapper that is particularly efficient for DNS (Domain Name System) and subdomain enumeration.
Pros
- Actively maintained and updated to keep up with the latest techniques and methodologies
- Backed by OWASP
- Good documentation
- Combines various reconnaissance and gathering techniques
- Similar features as Nmap, even on the scripting language
Cons
- While the commands are straightforward, analyzing the data will be hard for beginners
Other Penetration Testing Technologies
There are a number of complementary technologies often used by organizations to address security holes. Breach and attack simulation, for example, can be something of an automated, continuous pentesting tool. Others include vulnerability scanning tools and vulnerability management solutions. And IT asset management and patch management are important tools for staying on top of known vulnerabilities.
Cyber criminals are constantly adjusting their tactics to maximize effectiveness. Hence, penetration testing is an evolving field. Here are some of the top trends, defenses and tactics to keep in mind:
- Testing the external attack surface is necessary, as more assets are exposed to the internet and are regularly changing.
- Greater test frequency is needed to align with software development sprints.
- Penetration testing as a service (PTaas) provides integration with organizational defect tracking systems and can programmatically submit vulnerabilities to be tracked and remediated through the development team’s defect tracking system.
- DevOps also needs to perform pentesting, as development and security have become intertwined.
- Automation should be used where possible to close the security gap and speed up the remediation process.
- Testing the supply chain is a necessary response to breaches such as SolarWinds and Kaseya.
Bottom Line: Open-Source Penetration Testing Tools
Penetration testing is a critically important practice for keeping networks safe from intruders. While there are some comprehensive paid offerings, many pentesting teams prefer the widely used open-source tools that they’re already familiar with. With a wide range of open-source tools to choose from, pentesters can accomplish comprehensive testing of their environments by using a number of free tools. But whether you use open-source tools, commercial tools, or even third-party services, pentesting is something every organization with a network needs to do regularly.
Also read:
- 10 Best Open-Source Vulnerability Scanners for 2023
- Nmap Vulnerability Scanning Made Easy: Tutorial
- Getting Started with the Burp Suite: A Pentesting Tutorial
- Getting Started With the Metasploit Framework: A Pentesting Tutorial
This updates a February 2022 article by Julien Maury.
The post 24 Top Open Source Penetration Testing Tools appeared first on eSecurityPlanet.
]]>The post How to Use Input Sanitization to Prevent Web Attacks appeared first on eSecurityPlanet.
]]>Attackers have been using classic flaws for years with a pretty high success rate. While advanced threat actors have more sophisticated approaches such as adversarial machine learning, advanced obfuscation, and zero-day exploits, classic attack techniques such as SQL injection, cross-site scripting (XSS), remote file inclusion (RFI) and directory traversal are still the most common attacks.
These techniques are often the first step on the way to privilege escalation and lateral movements. That’s why developers must sanitize and validate data correctly before processing transactions or saving any entry in a database.
Here we’ll focus on sanitizing and validating inputs, but other elements such as a server’s configurations must also be taken into account to properly secure forms.
See the Top Web Application Firewall (WAF) Solutions
What is the Difference Between Sanitizing and Validating Input?
Validation checks whether an input — say on a web form — complies with specific policies and constraints (for example, single quotation marks). For example, consider the following input:
<input id="num" name="num" type="number" />
If there’s no validation, nothing prevents an attacker from exploiting the form by entering unexpected inputs instead of an expected number. He or she could also try to execute code directly if submitted forms are stored in a database, which is pretty common.
To prevent such a bad situation, developers must add a validation step where the data is inspected before proceeding. For example, using a popular language like PHP, you can check the data type, the length, and many other criteria.
Sanitizing consists of removing any unsafe characters from user inputs, and validating will check to see if the data is in the expected format and type. Sanitizing modifies the input to ensure it’s in a valid format for display, or before insertion in a database.
Why You Should Use Input Sanitization and Validation
The most common techniques used against weak inputs are probably cross-site scripting (XSS) attacks, which involves attackers injecting malicious scripts into otherwise trustworthy websites.
Some XSS attacks are more obvious than others, which means that even if you take the time to sanitize and validate your inputs, a skilled attacker might still find a way to inject malicious code under specific conditions.
A classic attack demo consists of injecting the following script in a weak input, where the placeholder ‘XSS’ is arbitrary JavaScript:
<script>alert('XSS')</script>
If the content of the input is displayed on the page (or elsewhere), the attacker can execute arbitrary JavaScript on the targeted website. The typical case is a vulnerable search input that displays the search term on the page:
https://mysite.com/?s=<script>alert('XSS')</script>
It gets worse if the malicious entry is stored in the database. The demo code might look fun to play with, but in real-world conditions attackers can do a lot of things with JavaScript, sometimes even steal cookies.
When Not to Use Sanitization
The biggest problem with sanitization is the false impression of security it might give. Stripping unwanted chars and HTML tags is only one layer of checking. It’s often poorly executed and removes too much information like legitimate quotes and special chars while it does not cover all angles of attack. You cannot apply generic rules blindly.
The context is the key, which includes the programming languages in use. More on this later, but it’s important to follow a principle called “escape late” (for example, just before output) because you know the exact context where the data is used.
In my experience, the trickiest situations are when you need to allow raw inputs and other permissive configurations. In such cases, it becomes very hard to sanitize data correctly, and you have to maintain a custom whitelist of allowed characters or manually blacklist some malicious patterns.
It’s recommended to use robust libraries and frameworks instead.
More generally, developers must not hesitate to return errors on bad inputs instead of resorting to guessing or fixing, which is prone to errors and flaws.
Best Practices: Sanitizing Inputs, Validation, Strict Mode
There are some principles and best practices that dev teams can follow for the best possible results. We’ll cover the broad categories, along with specifics to watch for.
Don’t Trust User Inputs
Some websites don’t bother checking user inputs, which exposes the application to the maximum level of danger. Fortunately, that’s getting rarer thanks to security awareness and code analysis. However, incomplete sanitization is not a great solution either.
Here are a few of the possible attack paths you need to think about.
GET requests
If developers don’t sanitize strings correctly, attackers can take advantage of XSS flaws such as:
https://mysite.com/?s=<script>console.log('you are in trouble!');</script>
Classic cybersecurity awareness usually highlights the above example with a simple console.log or even an alert. However, it shows that anyone can execute arbitrary JavaScript on your page by simply sending a shortened version of the malformed URL to unsuspecting victims.
Some XSS flaws can even be persistent (stored in the database, for example), which removes the hassle from attackers of making the victim click on something by automatically serving malicious payloads to the website’s users.
Cookies
Websites often use HTTP cookies for session management, customization, and tracking. For example, developers can log in users, remember their preferences, and analyze their behaviors.
The server generates a cookie, or an approximate piece of data, and sends it to the browser to save it for later uses. As a result, stealing cookies allows attackers to be able to impersonate the victims by providing them with immediate access to the targeted accounts without login.
Moreover, hackers don’t have to compromise the victim’s computer. Because HTTP cookies are sent along with each request, attackers can intercept those requests to steal data during man-in-the-middle (MITM) attacks, for example.
A more sophisticated approach can use an XSS attack to insert malicious code into the targeted website to ultimately copy users’ cookies and perform harmful actions in their name.
While Google plans to phase out cookies in its Chrome browser next year, it’s still important to develop best practices for cybersecurity. For example, as of 2022, SSL (Secure Sockets Layer) is no longer an optional layer. However, if the code sends non-SSL requests, cookies will be sent in plain text, so make sure you are using SSL everywhere.
Another good practice is to always use the httpOnly attribute to prevent hijacking with JavaScript. The SameSite attribute is also recommended for developers.
While cookies are convenient for both users and developers, modern authentication and APIs allow better approaches. As storing data in client-side databases allows for many safety and privacy vulnerabilities, it’s better to implement other more secure practices instead.
POST requests
POST requests are server-side requests, so they do not expose data in the URL, for example, when you upload an image on your online account or when you submit a contact form, such as:
<form action="https://my-website.com/contact" method="POST">
A common misconception is that POST requests are more secure than GET requests. However, at most, POST requests are security through obscurity. While it is better to use POST requests for user modifications, it’s not great for security-related purposes, and it won’t harden security magically.
One very simple way to sanitize POST data from inputs in PHP could be through the commands:
filter_var($_POST['message'], FILTER_SANITIZE_STRING);
filter_var('[email protected]', FILTER_VALIDATE_EMAIL)
Another good practice in PHP is to use htmlentities() to escape any unwanted HTML character in a string.
As with cookies, always use SSL to encrypt data, so only TCP/IP information will be left unencrypted.
Directory traversal
If the codebase includes an image tag such as
<img src="/getImages?filename=image12.png" />
then hackers may try using
https://yourwebsite.com/getImages?filename=../../../etc/passwd
to gain access to users’ information.
However, if your server is configured correctly, such attempts to disclose confidential information will be blocked. You should also consider filtering user inputs and ensuring that only the expected formats and data types are transmitted.
Also read: Top Code Debugging and Code Security Tools
Don’t Trust Client-Side Validation
A common misconception, especially for beginners, is to rely on HTML and JavaScript only to validate forms data. While HTML allows defining patterns and required fields, such as setting a character limit or requiring specific fields to be filled, there is no HTML attribute or JavaScript code that can’t be modified on the client side.
Hackers might also submit the form using cURL or any HTTP client, so the client side is absolutely not a secure layer to validate forms.
Enable Strict Mode
Whenever you can, enable strict mode, whether it’s PHP, JavaScript or SQL, or any other language. However, as strict mode prevents lots of convenient syntaxes, it might be difficult to enable if you have a significant technical debt and legacy.
On the other hand, if you don’t code in strict mode, the engine starts making guesses and can even modify values automatically to make the code work. This opens up vulnerabilities hackers can utilize to inject malicious commands.
For example, in 2015, Andrew Nacin, a major contributor to WordPress, explained how a critical security bug could have been avoided just by enabling strict mode in SQL. He demonstrated how hackers could exploit a critical vulnerability by using four-byte characters to force MySQL truncation and then inject malicious code in the database.
While a simple solution to prevent such an attack would be to execute the command SET SESSION sql_mode = "STRICT_ALL_TABLES" it is impossible to enable this without breaking all websites powered by WordPress.
Consult the OWASP Web Testing Guide
OWASP, the Open Web Application Security Project, maintains a comprehensive documentation called the Web Security Testing Guide (WTSG) that includes input validation.
This guide offers information on how to test various injections and other sneaky attacks on inputs. The content is frequently updated, and there are detailed explanations for various scenarios.
For example, you can check out their page on Testing for Stored Cross Site Scripting to learn how persistent XSS works and how to reproduce the exploit.
Also read: OWASP Names a New Top Vulnerability for First Time in Years
Bottom Line: Sanitize, Validate, and Escape Late
Sanitizing and validating inputs is a mandatory dev practice but you cannot apply a generic solution to all entries. You have to consider the specific contexts to be able to block injections. Moreover, don’t store anything in the database without validating it, but also escape values before displaying them, as some injections can poison database records.
Another essential practice is to escape data as late as possible, preferably just before display. This way, you perfectly know the final context and there’s no way to leave data unescaped.
Lastly, spend time on fine-tuning static code analysis. This process can tend to generate a lot of false positives, such as XSS flaws that can’t be exploited; however, every single HTML attribute and tag that gets its value dynamically should be escaped.
While hackers won’t be able to exploit all tags to grab sensitive data or trick logged in users, you should still incorporate static analysis to prevent as many vulnerabilities as possible.
Read next:
The post How to Use Input Sanitization to Prevent Web Attacks appeared first on eSecurityPlanet.
]]>